#include "../include/secp256k1.h"#include "../include/secp256k1_preallocated.h"#include "assumptions.h"#include "util.h"#include "field_impl.h"#include "scalar_impl.h"#include "group_impl.h"#include "ecmult_impl.h"#include "ecmult_const_impl.h"#include "ecmult_gen_impl.h"#include "ecdsa_impl.h"#include "eckey_impl.h"#include "hash_impl.h"#include "scratch_impl.h"#include "selftest.h"
Go to the source code of this file.
Classes | |
| struct | secp256k1_context_struct |
Macros | |
| #define | SECP256K1_BUILD |
| #define | ARG_CHECK(cond) |
| #define | ARG_CHECK_NO_RETURN(cond) |
Variables | |
| const secp256k1_context * | secp256k1_context_no_precomp = &secp256k1_context_no_precomp_ |
| const secp256k1_nonce_function | secp256k1_nonce_function_rfc6979 = nonce_function_rfc6979 |
| const secp256k1_nonce_function | secp256k1_nonce_function_default = nonce_function_rfc6979 |
Macro Definition Documentation
◆ ARG_CHECK
| #define ARG_CHECK | ( | cond | ) |
Definition at line 34 of file secp256k1.c.
◆ ARG_CHECK_NO_RETURN
| #define ARG_CHECK_NO_RETURN | ( | cond | ) |
Definition at line 41 of file secp256k1.c.
◆ SECP256K1_BUILD
| #define SECP256K1_BUILD |
Definition at line 7 of file secp256k1.c.
Function Documentation
◆ secp256k1_context_clone()
| secp256k1_context * secp256k1_context_clone | ( | const secp256k1_context * | ctx | ) |
Copy a secp256k1 context object (into dynamically allocated memory).
This function uses malloc to allocate memory. It is guaranteed that malloc is called at most once for every call of this function. If you need to avoid dynamic memory allocation entirely, see the functions in secp256k1_preallocated.h.
Returns: a newly created context object. Args: ctx: an existing context to copy
Definition at line 128 of file secp256k1.c.
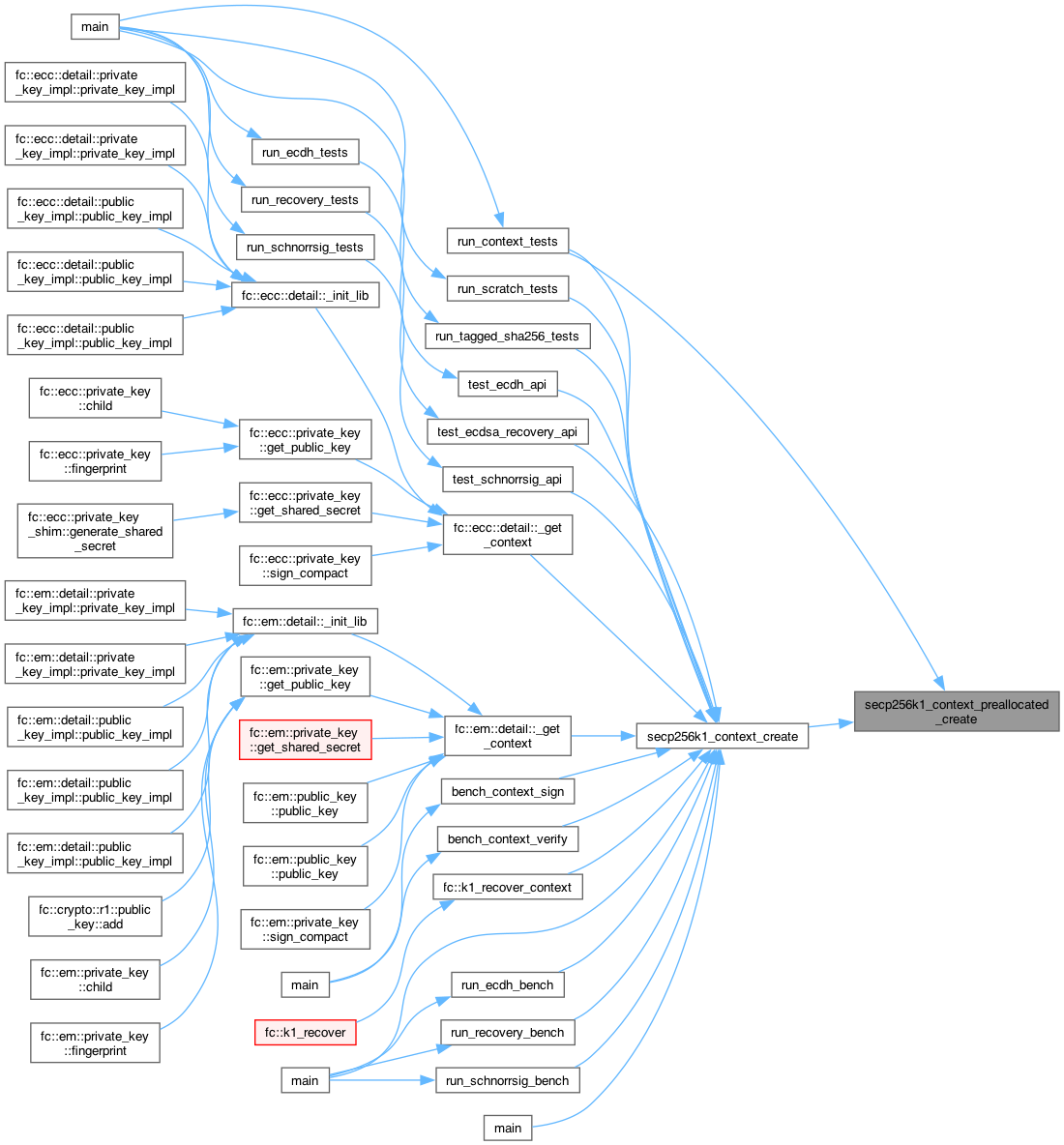
◆ secp256k1_context_create()
| secp256k1_context * secp256k1_context_create | ( | unsigned int | flags | ) |
Create a secp256k1 context object (in dynamically allocated memory).
This function uses malloc to allocate memory. It is guaranteed that malloc is called at most once for every call of this function. If you need to avoid dynamic memory allocation entirely, see the functions in secp256k1_preallocated.h.
Returns: a newly created context object. In: flags: which parts of the context to initialize.
See also secp256k1_context_randomize.
Definition at line 107 of file secp256k1.c.

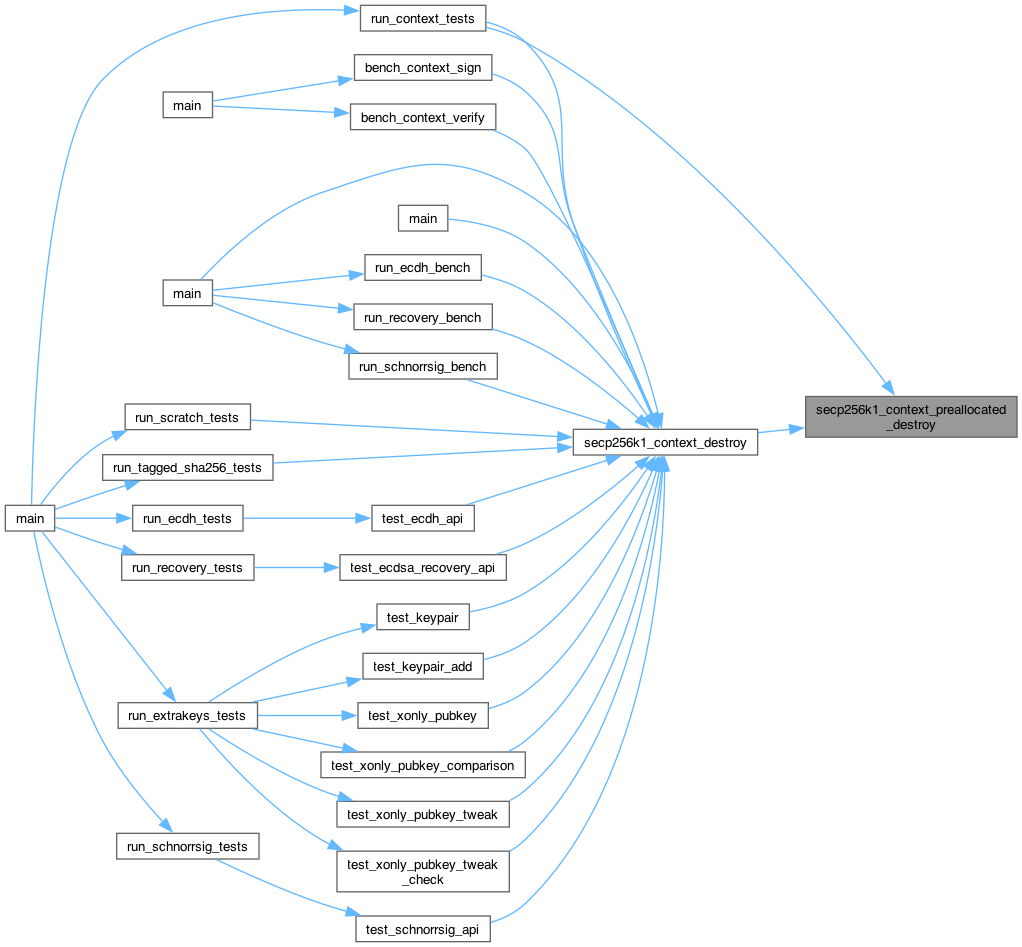
◆ secp256k1_context_destroy()
| void secp256k1_context_destroy | ( | secp256k1_context * | ctx | ) |
Destroy a secp256k1 context object (created in dynamically allocated memory).
The context pointer may not be used afterwards.
The context to destroy must have been created using secp256k1_context_create or secp256k1_context_clone. If the context has instead been created using secp256k1_context_preallocated_create or secp256k1_context_preallocated_clone, the behaviour is undefined. In that case, secp256k1_context_preallocated_destroy must be used instead.
Args: ctx: an existing context to destroy, constructed using secp256k1_context_create or secp256k1_context_clone
Definition at line 146 of file secp256k1.c.

◆ secp256k1_context_preallocated_clone()
| secp256k1_context * secp256k1_context_preallocated_clone | ( | const secp256k1_context * | ctx, |
| void * | prealloc ) |
Copy a secp256k1 context object into caller-provided memory.
The caller must provide a pointer to a rewritable contiguous block of memory of size at least secp256k1_context_preallocated_size(flags) bytes, suitably aligned to hold an object of any type.
The block of memory is exclusively owned by the created context object during the lifetime of this context object, see the description of secp256k1_context_preallocated_create for details.
Returns: a newly created context object. Args: ctx: an existing context to copy. In: prealloc: a pointer to a rewritable contiguous block of memory of size at least secp256k1_context_preallocated_size(flags) bytes, as detailed above.
Definition at line 118 of file secp256k1.c.
◆ secp256k1_context_preallocated_clone_size()
| size_t secp256k1_context_preallocated_clone_size | ( | const secp256k1_context * | ctx | ) |
Determine the memory size of a secp256k1 context object to be copied into caller-provided memory.
Returns: the required size of the caller-provided memory block. In: ctx: an existing context to copy.
Definition at line 76 of file secp256k1.c.
◆ secp256k1_context_preallocated_create()
| secp256k1_context * secp256k1_context_preallocated_create | ( | void * | prealloc, |
| unsigned int | flags ) |
Create a secp256k1 context object in caller-provided memory.
The caller must provide a pointer to a rewritable contiguous block of memory of size at least secp256k1_context_preallocated_size(flags) bytes, suitably aligned to hold an object of any type.
The block of memory is exclusively owned by the created context object during the lifetime of this context object, which begins with the call to this function and ends when a call to secp256k1_context_preallocated_destroy (which destroys the context object again) returns. During the lifetime of the context object, the caller is obligated not to access this block of memory, i.e., the caller may not read or write the memory, e.g., by copying the memory contents to a different location or trying to create a second context object in the memory. In simpler words, the prealloc pointer (or any pointer derived from it) should not be used during the lifetime of the context object.
Returns: a newly created context object. In: prealloc: a pointer to a rewritable contiguous block of memory of size at least secp256k1_context_preallocated_size(flags) bytes, as detailed above. flags: which parts of the context to initialize.
See also secp256k1_context_randomize (in secp256k1.h) and secp256k1_context_preallocated_destroy.
Definition at line 82 of file secp256k1.c.

◆ secp256k1_context_preallocated_destroy()
| void secp256k1_context_preallocated_destroy | ( | secp256k1_context * | ctx | ) |
Destroy a secp256k1 context object that has been created in caller-provided memory.
The context pointer may not be used afterwards.
The context to destroy must have been created using secp256k1_context_preallocated_create or secp256k1_context_preallocated_clone. If the context has instead been created using secp256k1_context_create or secp256k1_context_clone, the behaviour is undefined. In that case, secp256k1_context_destroy must be used instead.
If required, it is the responsibility of the caller to deallocate the block of memory properly after this function returns, e.g., by calling free on the preallocated pointer given to secp256k1_context_preallocated_create or secp256k1_context_preallocated_clone.
Args: ctx: an existing context to destroy, constructed using secp256k1_context_preallocated_create or secp256k1_context_preallocated_clone.
Definition at line 139 of file secp256k1.c.
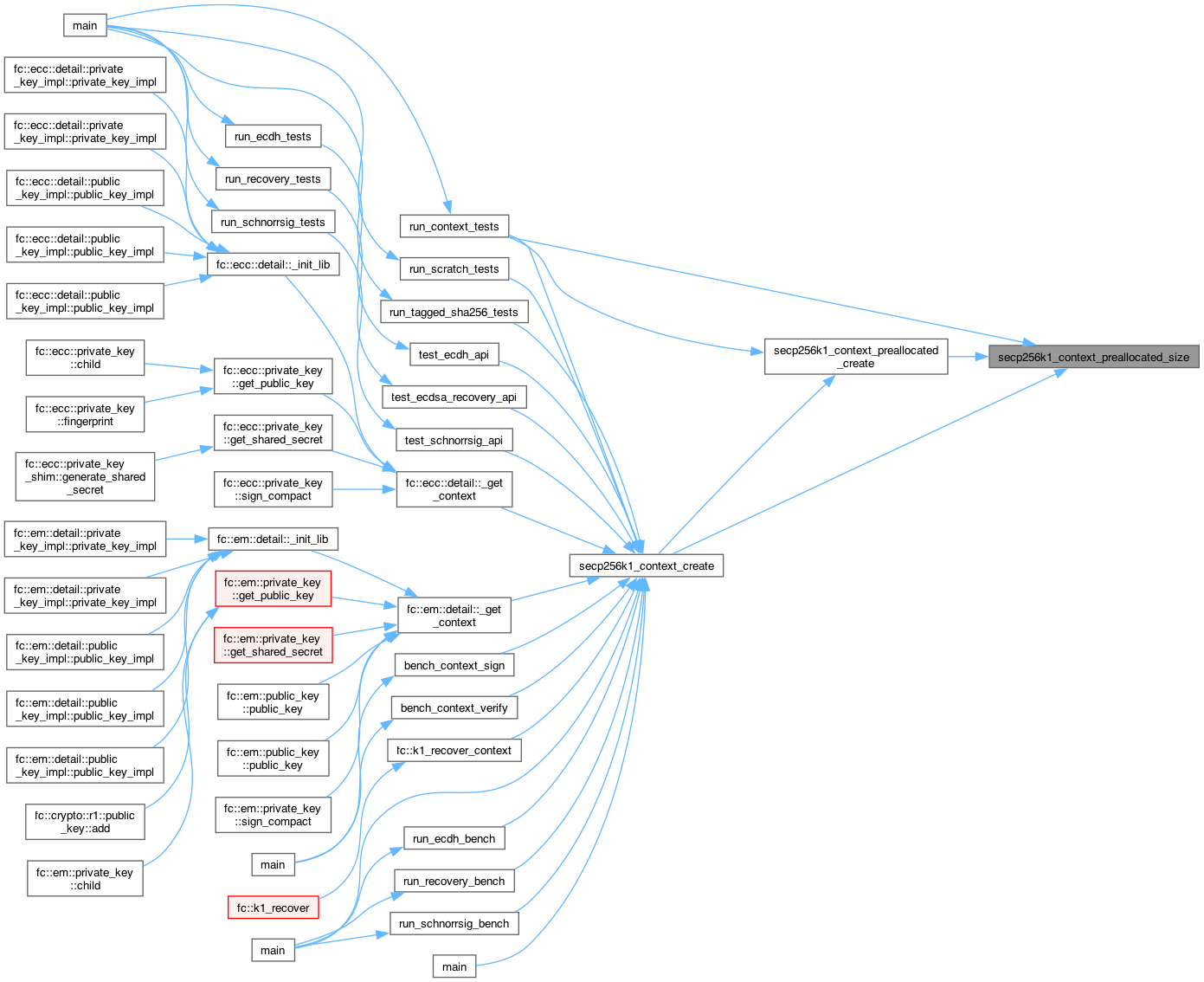
◆ secp256k1_context_preallocated_size()
| size_t secp256k1_context_preallocated_size | ( | unsigned int | flags | ) |
Determine the memory size of a secp256k1 context object to be created in caller-provided memory.
The purpose of this function is to determine how much memory must be provided to secp256k1_context_preallocated_create.
Returns: the required size of the caller-provided memory block In: flags: which parts of the context to initialize.
Definition at line 62 of file secp256k1.c.
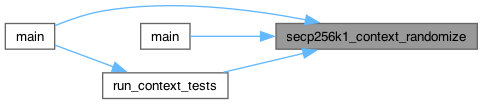
◆ secp256k1_context_randomize()
| int secp256k1_context_randomize | ( | secp256k1_context * | ctx, |
| const unsigned char * | seed32 ) |
Updates the context randomization to protect against side-channel leakage. Returns: 1: randomization successfully updated or nothing to randomize 0: error Args: ctx: pointer to a context object. In: seed32: pointer to a 32-byte random seed (NULL resets to initial state)
While secp256k1 code is written to be constant-time no matter what secret values are, it's possible that a future compiler may output code which isn't, and also that the CPU may not emit the same radio frequencies or draw the same amount power for all values.
This function provides a seed which is combined into the blinding value: that blinding value is added before each multiplication (and removed afterwards) so that it does not affect function results, but shields against attacks which rely on any input-dependent behaviour.
This function has currently an effect only on contexts initialized for signing because randomization is currently used only for signing. However, this is not guaranteed and may change in the future. It is safe to call this function on contexts not initialized for signing; then it will have no effect and return 1.
You should call this after secp256k1_context_create or secp256k1_context_clone (and secp256k1_context_preallocated_create or secp256k1_context_clone, resp.), and you may call this repeatedly afterwards.
Definition at line 706 of file secp256k1.c.
◆ secp256k1_context_set_error_callback()
| void secp256k1_context_set_error_callback | ( | secp256k1_context * | ctx, |
| void(* | fun )(const char *message, void *data), | ||
| const void * | data ) |
Set a callback function to be called when an internal consistency check fails. The default is crashing.
This can only trigger in case of a hardware failure, miscompilation, memory corruption, serious bug in the library, or other error would can otherwise result in undefined behaviour. It will not trigger due to mere incorrect usage of the API (see secp256k1_context_set_illegal_callback for that). After this callback returns, anything may happen, including crashing.
Args: ctx: an existing context object. In: fun: a pointer to a function to call when an internal error occurs, taking a message and an opaque pointer (NULL restores the default handler, see secp256k1_context_set_illegal_callback for details). data: the opaque pointer to pass to fun above, must be NULL for the default handler.
See also secp256k1_context_set_illegal_callback.
Definition at line 162 of file secp256k1.c.

◆ secp256k1_context_set_illegal_callback()
| void secp256k1_context_set_illegal_callback | ( | secp256k1_context * | ctx, |
| void(* | fun )(const char *message, void *data), | ||
| const void * | data ) |
Set a callback function to be called when an illegal argument is passed to an API call. It will only trigger for violations that are mentioned explicitly in the header.
The philosophy is that these shouldn't be dealt with through a specific return value, as calling code should not have branches to deal with the case that this code itself is broken.
On the other hand, during debug stage, one would want to be informed about such mistakes, and the default (crashing) may be inadvisable. When this callback is triggered, the API function called is guaranteed not to cause a crash, though its return value and output arguments are undefined.
When this function has not been called (or called with fn==NULL), then the default handler will be used. The library provides a default handler which writes the message to stderr and calls abort. This default handler can be replaced at link time if the preprocessor macro USE_EXTERNAL_DEFAULT_CALLBACKS is defined, which is the case if the build has been configured with –enable-external-default-callbacks. Then the following two symbols must be provided to link against:
- void secp256k1_default_illegal_callback_fn(const char* message, void* data);
- void secp256k1_default_error_callback_fn(const char* message, void* data); The library can call these default handlers even before a proper callback data pointer could have been set using secp256k1_context_set_illegal_callback or secp256k1_context_set_error_callback, e.g., when the creation of a context fails. In this case, the corresponding default handler will be called with the data pointer argument set to NULL.
Args: ctx: an existing context object. In: fun: a pointer to a function to call when an illegal argument is passed to the API, taking a message and an opaque pointer. (NULL restores the default handler.) data: the opaque pointer to pass to fun above, must be NULL for the default handler.
See also secp256k1_context_set_error_callback.
Definition at line 153 of file secp256k1.c.
◆ secp256k1_ec_privkey_negate()
| int secp256k1_ec_privkey_negate | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey ) |
Same as secp256k1_ec_seckey_negate, but DEPRECATED. Will be removed in future versions.
Definition at line 584 of file secp256k1.c.
◆ secp256k1_ec_privkey_tweak_add()
| int secp256k1_ec_privkey_tweak_add | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey, | ||
| const unsigned char * | tweak32 ) |
Same as secp256k1_ec_seckey_tweak_add, but DEPRECATED. Will be removed in future versions.
Definition at line 631 of file secp256k1.c.

◆ secp256k1_ec_privkey_tweak_mul()
| int secp256k1_ec_privkey_tweak_mul | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey, | ||
| const unsigned char * | tweak32 ) |
Same as secp256k1_ec_seckey_tweak_mul, but DEPRECATED. Will be removed in future versions.
Definition at line 679 of file secp256k1.c.

◆ secp256k1_ec_pubkey_cmp()
| int secp256k1_ec_pubkey_cmp | ( | const secp256k1_context * | ctx, |
| const secp256k1_pubkey * | pubkey1, | ||
| const secp256k1_pubkey * | pubkey2 ) |
Compare two public keys using lexicographic (of compressed serialization) order
Returns: <0 if the first public key is less than the second >0 if the first public key is greater than the second 0 if the two public keys are equal Args: ctx: a secp256k1 context object. In: pubkey1: first public key to compare pubkey2: second public key to compare
Definition at line 269 of file secp256k1.c.

◆ secp256k1_ec_pubkey_combine()
| int secp256k1_ec_pubkey_combine | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | out, | ||
| const secp256k1_pubkey *const * | ins, | ||
| size_t | n ) |
Add a number of public keys together.
Returns: 1: the sum of the public keys is valid. 0: the sum of the public keys is not valid. Args: ctx: pointer to a context object. Out: out: pointer to a public key object for placing the resulting public key. In: ins: pointer to array of pointers to public keys. n: the number of public keys to add together (must be at least 1).
Definition at line 714 of file secp256k1.c.
◆ secp256k1_ec_pubkey_create()
| int secp256k1_ec_pubkey_create | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | pubkey, | ||
| const unsigned char * | seckey ) |
Compute the public key for a secret key.
Returns: 1: secret was valid, public key stores. 0: secret was invalid, try again. Args: ctx: pointer to a context object, initialized for signing. Out: pubkey: pointer to the created public key. In: seckey: pointer to a 32-byte secret key.
Definition at line 551 of file secp256k1.c.
◆ secp256k1_ec_pubkey_negate()
| int secp256k1_ec_pubkey_negate | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | pubkey ) |
Negates a public key in place.
Returns: 1 always Args: ctx: pointer to a context object In/Out: pubkey: pointer to the public key to be negated.
Definition at line 588 of file secp256k1.c.

◆ secp256k1_ec_pubkey_parse()
| int secp256k1_ec_pubkey_parse | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | pubkey, | ||
| const unsigned char * | input, | ||
| size_t | inputlen ) |
Parse a variable-length public key into the pubkey object.
Returns: 1 if the public key was fully valid. 0 if the public key could not be parsed or is invalid. Args: ctx: a secp256k1 context object. Out: pubkey: pointer to a pubkey object. If 1 is returned, it is set to a parsed version of input. If not, its value is undefined. In: input: pointer to a serialized public key inputlen: length of the array pointed to by input
This function supports parsing compressed (33 bytes, header byte 0x02 or 0x03), uncompressed (65 bytes, header byte 0x04), or hybrid (65 bytes, header byte 0x06 or 0x07) format public keys.
Definition at line 228 of file secp256k1.c.
◆ secp256k1_ec_pubkey_serialize()
| int secp256k1_ec_pubkey_serialize | ( | const secp256k1_context * | ctx, |
| unsigned char * | output, | ||
| size_t * | outputlen, | ||
| const secp256k1_pubkey * | pubkey, | ||
| unsigned int | flags ) |
Serialize a pubkey object into a serialized byte sequence.
Returns: 1 always. Args: ctx: a secp256k1 context object. Out: output: a pointer to a 65-byte (if compressed==0) or 33-byte (if compressed==1) byte array to place the serialized key in. In/Out: outputlen: a pointer to an integer which is initially set to the size of output, and is overwritten with the written size. In: pubkey: a pointer to a secp256k1_pubkey containing an initialized public key. flags: SECP256K1_EC_COMPRESSED if serialization should be in compressed format, otherwise SECP256K1_EC_UNCOMPRESSED.
Definition at line 246 of file secp256k1.c.
◆ secp256k1_ec_pubkey_tweak_add()
| int secp256k1_ec_pubkey_tweak_add | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | pubkey, | ||
| const unsigned char * | tweak32 ) |
Tweak a public key by adding tweak times the generator to it.
Returns: 0 if the arguments are invalid or the resulting public key would be invalid (only when the tweak is the negation of the corresponding secret key). 1 otherwise. Args: ctx: pointer to a context object initialized for validation. In/Out: pubkey: pointer to a public key object. pubkey will be set to an invalid value if this function returns 0. In: tweak32: pointer to a 32-byte tweak. If the tweak is invalid according to secp256k1_ec_seckey_verify, this function returns 0. For uniformly random 32-byte arrays the chance of being invalid is negligible (around 1 in 2^128).
Definition at line 642 of file secp256k1.c.
◆ secp256k1_ec_pubkey_tweak_mul()
| int secp256k1_ec_pubkey_tweak_mul | ( | const secp256k1_context * | ctx, |
| secp256k1_pubkey * | pubkey, | ||
| const unsigned char * | tweak32 ) |
Tweak a public key by multiplying it by a tweak value.
Returns: 0 if the arguments are invalid. 1 otherwise. Args: ctx: pointer to a context object initialized for validation. In/Out: pubkey: pointer to a public key object. pubkey will be set to an invalid value if this function returns 0. In: tweak32: pointer to a 32-byte tweak. If the tweak is invalid according to secp256k1_ec_seckey_verify, this function returns 0. For uniformly random 32-byte arrays the chance of being invalid is negligible (around 1 in 2^128).
Definition at line 683 of file secp256k1.c.
◆ secp256k1_ec_seckey_negate()
| int secp256k1_ec_seckey_negate | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey ) |
Negates a secret key in place.
Returns: 0 if the given secret key is invalid according to secp256k1_ec_seckey_verify. 1 otherwise Args: ctx: pointer to a context object In/Out: seckey: pointer to the 32-byte secret key to be negated. If the secret key is invalid according to secp256k1_ec_seckey_verify, this function returns 0 and seckey will be set to some unspecified value.
Definition at line 569 of file secp256k1.c.
◆ secp256k1_ec_seckey_tweak_add()
| int secp256k1_ec_seckey_tweak_add | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey, | ||
| const unsigned char * | tweak32 ) |
Tweak a secret key by adding tweak to it.
Returns: 0 if the arguments are invalid or the resulting secret key would be invalid (only when the tweak is the negation of the secret key). 1 otherwise. Args: ctx: pointer to a context object. In/Out: seckey: pointer to a 32-byte secret key. If the secret key is invalid according to secp256k1_ec_seckey_verify, this function returns 0. seckey will be set to some unspecified value if this function returns 0. In: tweak32: pointer to a 32-byte tweak. If the tweak is invalid according to secp256k1_ec_seckey_verify, this function returns 0. For uniformly random 32-byte arrays the chance of being invalid is negligible (around 1 in 2^128).
Definition at line 615 of file secp256k1.c.
◆ secp256k1_ec_seckey_tweak_mul()
| int secp256k1_ec_seckey_tweak_mul | ( | const secp256k1_context * | ctx, |
| unsigned char * | seckey, | ||
| const unsigned char * | tweak32 ) |
Tweak a secret key by multiplying it by a tweak.
Returns: 0 if the arguments are invalid. 1 otherwise. Args: ctx: pointer to a context object. In/Out: seckey: pointer to a 32-byte secret key. If the secret key is invalid according to secp256k1_ec_seckey_verify, this function returns 0. seckey will be set to some unspecified value if this function returns 0. In: tweak32: pointer to a 32-byte tweak. If the tweak is invalid according to secp256k1_ec_seckey_verify, this function returns 0. For uniformly random 32-byte arrays the chance of being invalid is negligible (around 1 in 2^128).
Definition at line 659 of file secp256k1.c.
◆ secp256k1_ec_seckey_verify()
| int secp256k1_ec_seckey_verify | ( | const secp256k1_context * | ctx, |
| const unsigned char * | seckey ) |
Verify an ECDSA secret key.
A secret key is valid if it is not 0 and less than the secp256k1 curve order when interpreted as an integer (most significant byte first). The probability of choosing a 32-byte string uniformly at random which is an invalid secret key is negligible.
Returns: 1: secret key is valid 0: secret key is invalid Args: ctx: pointer to a context object. In: seckey: pointer to a 32-byte secret key.
Definition at line 528 of file secp256k1.c.
◆ secp256k1_ecdsa_sign()
| int secp256k1_ecdsa_sign | ( | const secp256k1_context * | ctx, |
| secp256k1_ecdsa_signature * | sig, | ||
| const unsigned char * | msghash32, | ||
| const unsigned char * | seckey, | ||
| secp256k1_nonce_function | noncefp, | ||
| const void * | ndata ) |
Create an ECDSA signature.
Returns: 1: signature created 0: the nonce generation function failed, or the secret key was invalid. Args: ctx: pointer to a context object, initialized for signing. Out: sig: pointer to an array where the signature will be placed. In: msghash32: the 32-byte message hash being signed. seckey: pointer to a 32-byte secret key. noncefp: pointer to a nonce generation function. If NULL, secp256k1_nonce_function_default is used. ndata: pointer to arbitrary data used by the nonce generation function (can be NULL). If it is non-NULL and secp256k1_nonce_function_default is used, then ndata must be a pointer to 32-bytes of additional data.
The created signature is always in lower-S form. See secp256k1_ecdsa_signature_normalize for more details.
Definition at line 514 of file secp256k1.c.
◆ secp256k1_ecdsa_signature_normalize()
| int secp256k1_ecdsa_signature_normalize | ( | const secp256k1_context * | ctx, |
| secp256k1_ecdsa_signature * | sigout, | ||
| const secp256k1_ecdsa_signature * | sigin ) |
Convert a signature to a normalized lower-S form.
Returns: 1 if sigin was not normalized, 0 if it already was. Args: ctx: a secp256k1 context object Out: sigout: a pointer to a signature to fill with the normalized form, or copy if the input was already normalized. (can be NULL if you're only interested in whether the input was already normalized). In: sigin: a pointer to a signature to check/normalize (can be identical to sigout)
With ECDSA a third-party can forge a second distinct signature of the same message, given a single initial signature, but without knowing the key. This is done by negating the S value modulo the order of the curve, 'flipping' the sign of the random point R which is not included in the signature.
Forgery of the same message isn't universally problematic, but in systems where message malleability or uniqueness of signatures is important this can cause issues. This forgery can be blocked by all verifiers forcing signers to use a normalized form.
The lower-S form reduces the size of signatures slightly on average when variable length encodings (such as DER) are used and is cheap to verify, making it a good choice. Security of always using lower-S is assured because anyone can trivially modify a signature after the fact to enforce this property anyway.
The lower S value is always between 0x1 and 0x7FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF5D576E7357A4501DDFE92F46681B20A0, inclusive.
No other forms of ECDSA malleability are known and none seem likely, but there is no formal proof that ECDSA, even with this additional restriction, is free of other malleability. Commonly used serialization schemes will also accept various non-unique encodings, so care should be taken when this property is required for an application.
The secp256k1_ecdsa_sign function will by default create signatures in the lower-S form, and secp256k1_ecdsa_verify will not accept others. In case signatures come from a system that cannot enforce this property, secp256k1_ecdsa_signature_normalize must be called before verification.
Definition at line 381 of file secp256k1.c.

◆ secp256k1_ecdsa_signature_parse_compact()
| int secp256k1_ecdsa_signature_parse_compact | ( | const secp256k1_context * | ctx, |
| secp256k1_ecdsa_signature * | sig, | ||
| const unsigned char * | input64 ) |
Parse an ECDSA signature in compact (64 bytes) format.
Returns: 1 when the signature could be parsed, 0 otherwise. Args: ctx: a secp256k1 context object Out: sig: a pointer to a signature object In: input64: a pointer to the 64-byte array to parse
The signature must consist of a 32-byte big endian R value, followed by a 32-byte big endian S value. If R or S fall outside of [0..order-1], the encoding is invalid. R and S with value 0 are allowed in the encoding.
After the call, sig will always be initialized. If parsing failed or R or S are zero, the resulting sig value is guaranteed to fail validation for any message and public key.
Definition at line 335 of file secp256k1.c.

◆ secp256k1_ecdsa_signature_parse_der()
| int secp256k1_ecdsa_signature_parse_der | ( | const secp256k1_context * | ctx, |
| secp256k1_ecdsa_signature * | sig, | ||
| const unsigned char * | input, | ||
| size_t | inputlen ) |
Parse a DER ECDSA signature.
Returns: 1 when the signature could be parsed, 0 otherwise. Args: ctx: a secp256k1 context object Out: sig: a pointer to a signature object In: input: a pointer to the signature to be parsed inputlen: the length of the array pointed to be input
This function will accept any valid DER encoded signature, even if the encoded numbers are out of range.
After the call, sig will always be initialized. If parsing failed or the encoded numbers are out of range, signature validation with it is guaranteed to fail for every message and public key.
Definition at line 319 of file secp256k1.c.
◆ secp256k1_ecdsa_signature_serialize_compact()
| int secp256k1_ecdsa_signature_serialize_compact | ( | const secp256k1_context * | ctx, |
| unsigned char * | output64, | ||
| const secp256k1_ecdsa_signature * | sig ) |
Serialize an ECDSA signature in compact (64 byte) format.
Returns: 1 Args: ctx: a secp256k1 context object Out: output64: a pointer to a 64-byte array to store the compact serialization In: sig: a pointer to an initialized signature object
See secp256k1_ecdsa_signature_parse_compact for details about the encoding.
Definition at line 368 of file secp256k1.c.
◆ secp256k1_ecdsa_signature_serialize_der()
| int secp256k1_ecdsa_signature_serialize_der | ( | const secp256k1_context * | ctx, |
| unsigned char * | output, | ||
| size_t * | outputlen, | ||
| const secp256k1_ecdsa_signature * | sig ) |
Serialize an ECDSA signature in DER format.
Returns: 1 if enough space was available to serialize, 0 otherwise Args: ctx: a secp256k1 context object Out: output: a pointer to an array to store the DER serialization In/Out: outputlen: a pointer to a length integer. Initially, this integer should be set to the length of output. After the call it will be set to the length of the serialization (even if 0 was returned). In: sig: a pointer to an initialized signature object
Definition at line 356 of file secp256k1.c.
◆ secp256k1_ecdsa_verify()
| int secp256k1_ecdsa_verify | ( | const secp256k1_context * | ctx, |
| const secp256k1_ecdsa_signature * | sig, | ||
| const unsigned char * | msghash32, | ||
| const secp256k1_pubkey * | pubkey ) |
Verify an ECDSA signature.
Returns: 1: correct signature 0: incorrect or unparseable signature Args: ctx: a secp256k1 context object, initialized for verification. In: sig: the signature being verified. msghash32: the 32-byte message hash being verified. The verifier must make sure to apply a cryptographic hash function to the message by itself and not accept an msghash32 value directly. Otherwise, it would be easy to create a "valid" signature without knowledge of the secret key. See also https://bitcoin.stackexchange.com/a/81116/35586 for more background on this topic. pubkey: pointer to an initialized public key to verify with.
To avoid accepting malleable signatures, only ECDSA signatures in lower-S form are accepted.
If you need to accept ECDSA signatures from sources that do not obey this rule, apply secp256k1_ecdsa_signature_normalize to the signature prior to validation, but be aware that doing so results in malleable signatures.
For details, see the comments for that function.
Definition at line 400 of file secp256k1.c.
◆ secp256k1_scratch_space_create()
| secp256k1_scratch_space * secp256k1_scratch_space_create | ( | const secp256k1_context * | ctx, |
| size_t | size ) |
Create a secp256k1 scratch space object.
Returns: a newly created scratch space. Args: ctx: an existing context object. In: size: amount of memory to be available as scratch space. Some extra (<100 bytes) will be allocated for extra accounting.
Definition at line 171 of file secp256k1.c.
◆ secp256k1_scratch_space_destroy()
| void secp256k1_scratch_space_destroy | ( | const secp256k1_context * | ctx, |
| secp256k1_scratch_space * | scratch ) |
Destroy a secp256k1 scratch space.
The pointer may not be used afterwards. Args: ctx: a secp256k1 context object. scratch: space to destroy
Definition at line 176 of file secp256k1.c.
◆ secp256k1_tagged_sha256()
| int secp256k1_tagged_sha256 | ( | const secp256k1_context * | ctx, |
| unsigned char * | hash32, | ||
| const unsigned char * | tag, | ||
| size_t | taglen, | ||
| const unsigned char * | msg, | ||
| size_t | msglen ) |
Compute a tagged hash as defined in BIP-340.
This is useful for creating a message hash and achieving domain separation through an application-specific tag. This function returns SHA256(SHA256(tag)||SHA256(tag)||msg). Therefore, tagged hash implementations optimized for a specific tag can precompute the SHA256 state after hashing the tag hashes.
Returns: 1 always. Args: ctx: pointer to a context object Out: hash32: pointer to a 32-byte array to store the resulting hash In: tag: pointer to an array containing the tag taglen: length of the tag array msg: pointer to an array containing the message msglen: length of the message array
Definition at line 740 of file secp256k1.c.
Variable Documentation
◆ secp256k1_context_no_precomp
| const secp256k1_context* secp256k1_context_no_precomp = &secp256k1_context_no_precomp_ |
A simple secp256k1 context object with no precomputed tables. These are useful for type serialization/parsing functions which require a context object to maintain API consistency, but currently do not require expensive precomputations or dynamic allocations.
Definition at line 60 of file secp256k1.c.
◆ secp256k1_nonce_function_default
| const secp256k1_nonce_function secp256k1_nonce_function_default = nonce_function_rfc6979 |
A default safe nonce generation function (currently equal to secp256k1_nonce_function_rfc6979).
Definition at line 456 of file secp256k1.c.
◆ secp256k1_nonce_function_rfc6979
| const secp256k1_nonce_function secp256k1_nonce_function_rfc6979 = nonce_function_rfc6979 |
An implementation of RFC6979 (using HMAC-SHA256) as nonce generation function. If a data pointer is passed, it is assumed to be a pointer to 32 bytes of extra entropy.
Definition at line 455 of file secp256k1.c.