2111 {
2112
2115
2116 struct {
2120 const char *special;
2121 } benchmarks[] = {
2160 {0, 0, 8, "Random 8 bytes"},
2161 {0, 0, 16, "Random 16 bytes"},
2162 {0, 0, 32, "Random 32 bytes"},
2163 {0, 0, 64, "Random 64 bytes"},
2164 {0, 0, 128, "Random 128 bytes"},
2165 {0, 0, 256, "Random 256 bytes"},
2166 {0, 0, 512, "Random 512 bytes"},
2167 {0, 0, 1024, "Random 1024 bytes"},
2169 };
2170
2171
2173 "\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f";
2174 const uint8_t otp_id[] =
"\x01\x02\x03\x04\x05\x06";
2176 "\x2f\x5d\x71\xa4\x91\x5d\xec\x30\x4a\xa1\x3c\xcf\x97\xbb\x0d\xbb";
2177 const uint8_t password[] =
"benchmark";
2178
2179 if (
argv[1].d == 0) {
2180 fprintf(stderr, "Benchmark with 0 rounds seems pointless\n");
2181 return -1;
2182 }
2183
2184 for (size_t i = 0; i < sizeof(benchmarks) / sizeof(benchmarks[0]); i++) {
2185 struct timeval total = {0, 0};
2186 struct timeval avg = {0, 0};
2187 struct timeval max = {0, 0};
2192 size_t algo_len = sizeof(algo_data);
2193 const char *str1 = NULL, *str2 = "", *str3 = "";
2197#ifndef _WIN32
2198 size_t chars = 0;
2199#endif
2200
2201 if (
argv[3].
a != 0) {
2202 if (
argv[3].
a != benchmarks[i].algo &&
argv[3].
a != benchmarks[i].algo2) {
2203 continue;
2204 }
2205 }
2206 if (benchmarks[i].algo) {
2208 }
2209 if (benchmarks[i].algo2) {
2210 str2 = " ";
2212 }
2213 if (str1) {
2215 }
2216
2217 if (str1) {
2218#ifndef _WIN32
2219 chars =
2220#endif
2221 fprintf(stderr, "Doing benchmark setup for %s%s%s...", str1, str2,
2222 str3);
2223 }
2224
2234 } else {
2235 fprintf(stderr, "Unknown benchmark algorithms\n");
2236 return -1;
2237 }
2241 }
else if (
yh_is_ec(benchmarks[i].algo)) {
2251
2253 fprintf(stderr, "Failed ECDH setup\n");
2254 return -1;
2255 }
2256 algo_len--;
2260 fprintf(stderr, "Failed to get ECDH pubkey (%zu)\n", algo_len);
2261 return -1;
2262 }
2263 algo_data[0] = 0x04;
2264 algo_len++;
2267 fprintf(stderr, "Failed deleting temporary ec key\n");
2268 return -1;
2269 }
2270 } else {
2271 fprintf(stderr, "Unknown benchmark algorithms\n");
2272 return -1;
2273 }
2282 str2 = " ";
2283 str3 = benchmarks[i].special;
2305 0x12345678);
2308 &algo_len);
2309 }
2310 } else if (strncmp(benchmarks[i].special, "Random ", 7) == 0) {
2311 str1 = benchmarks[i].special;
2318 password, sizeof(password));
2319 } else {
2320 fprintf(stderr, "Unknown benchmark algorithms\n");
2321 return -1;
2322 }
2323
2325 fprintf(stderr, "Failed benchmark setup for %s%s%s\n", str1, str2, str3);
2326 return -1;
2327 }
2328
2329 memset(&min, 0x7f,
sizeof(min));
2334 struct timeval before, after, result;
2335
2336 memset(data,
j,
sizeof(data));
2337 gettimeofday(&before, NULL);
2343 benchmarks[i].bytes, out, &
out_len);
2344 }
else if (
yh_is_rsa(benchmarks[i].algo) &&
2351 }
else if (
yh_is_ec(benchmarks[i].algo) &&
2358 }
else if (
yh_is_ec(benchmarks[i].algo) &&
2377 NULL, NULL, NULL);
2378 } else if (strncmp(benchmarks[i].special, "Random ", 7) == 0) {
2384 sizeof(password),
false, &
ses);
2387 }
2390 }
2391 } else {
2392 fprintf(stderr, "Unknown benchmark algorithm\n");
2393 return -1;
2394 }
2395
2396 gettimeofday(&after, NULL);
2397
2399 fprintf(stderr,
"Failed running benchmark %u for %s%s%s\n",
j, str1,
2400 str2, str3);
2401 return -1;
2402 }
2403
2404 time_elapsed(&after, &before, &result);
2405 if (time_less(&result, &min)) {
2407 }
2408 if (time_less(&max, &result)) {
2409 max = result;
2410 }
2411 time_add(&result, &total, &total);
2412 time_average(&total,
j + 1, &avg);
2413#ifndef _WIN32
2414 struct winsize w;
2415 ioctl(fileno(stderr), TIOCGWINSZ, &w);
2416
2417 if (chars > w.ws_col) {
2418
2419 fprintf(stderr, "\33[%zuF", chars / w.ws_col);
2420 } else {
2421
2422 fprintf(stderr, "\33[1G");
2423 }
2424
2425 fprintf(stderr, "\33[J");
2426 chars = fprintf(stderr,
2427 "%s%s%s (%u/%d times) total: %ld.%06ld avg: %ld.%06ld "
2428 "min: %ld.%06ld max: %ld.%06ld tps: %.06f",
2429 str1, str2, str3,
j + 1,
argv[1].w, total.tv_sec,
2430 (long) total.tv_usec, avg.tv_sec, (long) avg.tv_usec,
2431 min.tv_sec, (
long)
min.tv_usec, max.tv_sec,
2432 (
long) max.tv_usec, time_tps(&total,
j + 1));
2433 fflush(stderr);
2434#endif
2435 }
2436#ifdef _WIN32
2437 fprintf(stderr,
2438 "%s%s%s (%d times) total: %ld.%06ld avg: %ld.%06ld "
2439 "min: %ld.%06ld max: %ld.%06ld tps: %.06f",
2440 str1, str2, str3,
argv[1].w, total.tv_sec, (
long) total.tv_usec,
2441 avg.tv_sec, (
long) avg.tv_usec,
min.tv_sec, (
long)
min.tv_usec,
2442 max.tv_sec, (
long) max.tv_usec, time_tps(&total,
argv[1].w));
2443
2444#endif
2445 fprintf(stderr, "\n");
2446 if (type != 0) {
2448 }
2449 }
2450
2451 return 0;
2452}
const T & min(const T &a, const T &b)
const GenericPointer< typename T::ValueType > T2 T::AllocatorType & a
Capabilities representation.
bool yh_is_rsa(yh_algorithm algorithm)
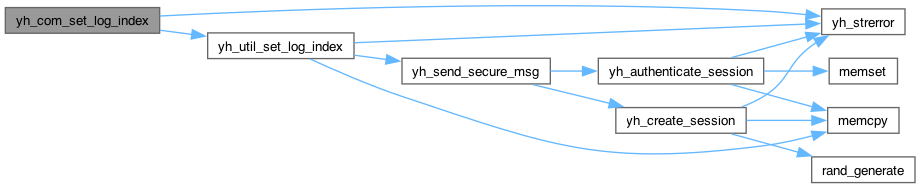
yh_rc yh_util_generate_hmac_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm)
yh_rc yh_util_generate_wrap_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm, const yh_capabilities *delegated_capabilities)
yh_rc yh_util_derive_ecdh(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
yh_rc yh_algo_to_string(yh_algorithm algo, char const **result)
yh_rc yh_util_generate_ec_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm)
bool yh_is_ec(yh_algorithm algorithm)
yh_rc yh_util_decrypt_otp(yh_session *session, uint16_t key_id, const uint8_t *aead, size_t aead_len, const uint8_t *otp, uint16_t *useCtr, uint8_t *sessionCtr, uint8_t *tstph, uint16_t *tstpl)
yh_rc yh_create_session_derived(yh_connector *connector, uint16_t authkey_id, const uint8_t *password, size_t password_len, bool recreate, yh_session **session)
yh_rc yh_util_generate_ed_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm)
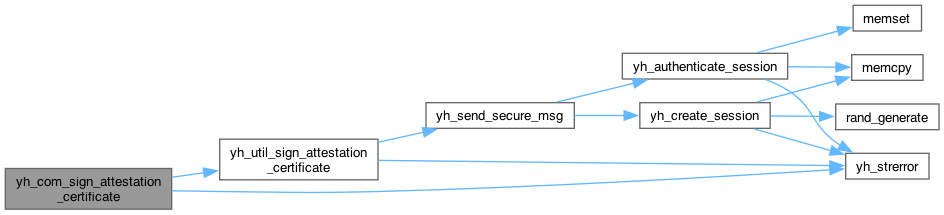
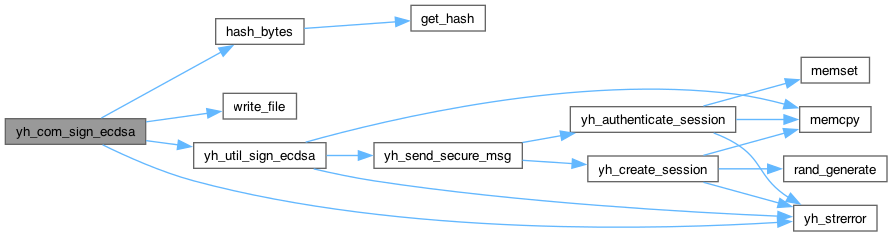
yh_rc yh_util_sign_ecdsa(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
yh_rc yh_util_close_session(yh_session *session)
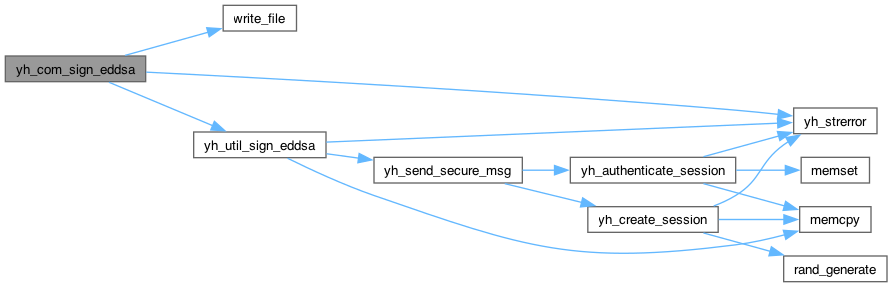
yh_rc yh_util_sign_eddsa(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
yh_rc yh_authenticate_session(yh_session *session)
yh_rc yh_util_import_authentication_key_derived(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, const yh_capabilities *delegated_capabilities, const uint8_t *password, size_t password_len)
yh_rc yh_util_create_otp_aead(yh_session *session, uint16_t key_id, const uint8_t *key, const uint8_t *private_id, uint8_t *out, size_t *out_len)
yh_rc yh_util_sign_hmac(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
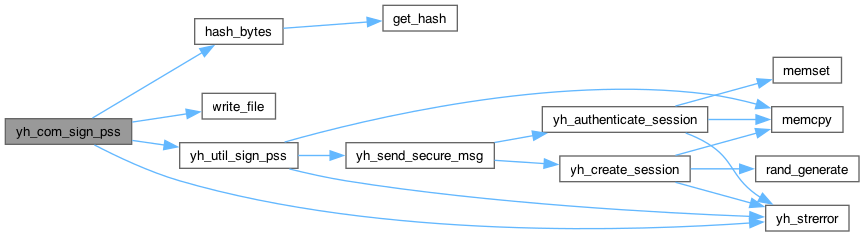
yh_rc yh_util_sign_pss(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len, size_t salt_len, yh_algorithm mgf1Algo)
yh_rc yh_util_generate_otp_aead_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm, uint32_t nonce_id)
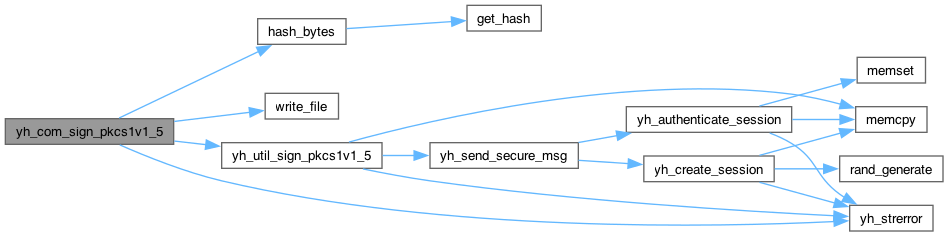
yh_rc yh_util_sign_pkcs1v1_5(yh_session *session, uint16_t key_id, bool hashed, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
yh_rc yh_util_export_wrapped(yh_session *session, uint16_t wrapping_key_id, yh_object_type target_type, uint16_t target_id, uint8_t *out, size_t *out_len)
yh_rc yh_util_get_public_key(yh_session *session, uint16_t id, uint8_t *data, size_t *data_len, yh_algorithm *algorithm)
yh_rc yh_string_to_capabilities(const char *capability, yh_capabilities *result)
yh_rc yh_util_generate_rsa_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm)
bool yh_is_hmac(yh_algorithm algorithm)
yh_rc yh_util_delete_object(yh_session *session, uint16_t id, yh_object_type type)
yh_rc yh_util_get_pseudo_random(yh_session *session, size_t len, uint8_t *out, size_t *out_len)
@ YH_OTP_AEAD_KEY
OTP AEAD Key is a secret key used to decrypt Yubico OTP values.
@ YH_HMAC_KEY
HMAC Key is a secret key used when computing and verifying HMAC signatures.
@ YH_ASYMMETRIC_KEY
Asymmetric Key is the private key of an asymmetric key-pair.
@ YH_AUTHENTICATION_KEY
Authentication Key is used to establish Sessions with a device.
#define YH_OBJ_LABEL_LEN
Max length of object labels.
@ YH_ALGO_RSA_PSS_SHA384
rsa-pss-sha384
@ YH_ALGO_RSA_PKCS1_SHA256
rsa-pkcs1-sha256
@ YH_ALGO_RSA_PSS_SHA512
rsa-pss-sha512
@ YH_ALGO_EC_BP384
ecbp384
@ YH_ALGO_EC_ECDSA_SHA256
ecdsa-sha256
@ YH_ALGO_EC_ECDSA_SHA512
ecdsa-sha512
@ YH_ALGO_AES128_YUBICO_AUTHENTICATION
aes128-yubico-authentication
@ YH_ALGO_AES192_YUBICO_OTP
aes192-yubico-otp
@ YH_ALGO_AES128_YUBICO_OTP
aes128-yubico-otp
@ YH_ALGO_EC_ECDSA_SHA384
ecdsa-sha384
@ YH_ALGO_EC_ED25519
ed25519
@ YH_ALGO_HMAC_SHA512
hmac-sha512
@ YH_ALGO_HMAC_SHA384
hmac-sha384
@ YH_ALGO_RSA_PKCS1_SHA512
rsa-pkcs1-sha512
@ YH_ALGO_AES256_CCM_WRAP
aes256-ccm-wrap
@ YH_ALGO_HMAC_SHA1
hmac-sha1
@ YH_ALGO_RSA_2048
rsa2048
@ YH_ALGO_HMAC_SHA256
hmac-sha256
@ YH_ALGO_AES192_CCM_WRAP
aes192-ccm-wrap
@ YH_ALGO_EC_BP512
ecbp512
@ YH_ALGO_EC_BP256
ecbp256
@ YH_ALGO_RSA_PSS_SHA256
rsa-pss-sha256
@ YH_ALGO_AES256_YUBICO_OTP
aes256-yubico-otp
@ YH_ALGO_MGF1_SHA1
mgf1-sha1
@ YH_ALGO_AES128_CCM_WRAP
aes128-ccm-wrap
@ YH_ALGO_RSA_4096
rsa4096
@ YH_ALGO_EC_ECDSA_SHA1
ecdsa-sha1
@ YH_ALGO_RSA_PKCS1_SHA384
rsa-pkcs1-sha384
@ YH_ALGO_RSA_3072
rsa3072
yh_capabilities capabilities
memset(pInfo->slotDescription, ' ', 64)