Loading...
Searching...
No Matches
#include <stdlib.h>#include <yubihsm.h>#include <sys/time.h>#include <stdint.h>#include <string.h>#include <stdio.h>
Include dependency graph for yubihsm_shell_tests.c:
Go to the source code of this file.
Classes | |
| struct | repetition_stats |
Macros | |
| #define | EXIT_SKIPPED 77; |
| #define | DEFAULT_KEY "\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f" |
| #define | N_REPS 8 |
| #define | N_ITERATIONS 1000 |
| #define | ECHO_BYTE 0x0f |
Functions | |
| int | main () |
Variables | |
| yh_device ** | devices |
| uint16_t | n_devices |
| yh_session * | ses |
Macro Definition Documentation
◆ DEFAULT_KEY
| #define DEFAULT_KEY "\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f" |
Definition at line 37 of file yubihsm_shell_tests.c.
37#define DEFAULT_KEY \
38 "\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f"
◆ ECHO_BYTE
| #define ECHO_BYTE 0x0f |
Definition at line 43 of file yubihsm_shell_tests.c.
◆ EXIT_SKIPPED
| #define EXIT_SKIPPED 77; |
Definition at line 24 of file yubihsm_shell_tests.c.
◆ N_ITERATIONS
| #define N_ITERATIONS 1000 |
Definition at line 42 of file yubihsm_shell_tests.c.
◆ N_REPS
| #define N_REPS 8 |
Definition at line 40 of file yubihsm_shell_tests.c.
40#define N_REPS \
41 8 // Data length for repetition i is 2^(1 + i) for i in [0, N_REPS-1]
Function Documentation
◆ main()
| int main | ( | void | ) |
Definition at line 45 of file yubihsm_shell_tests.c.
45 {
46
48
52
54
56
57 struct timeval before, after;
58 double this;
60
63 uint16_t response_len;
65
67 // | YH_VERB_INFO | YH_VERB_ERR;
68
71 fprintf(stderr, "Unable to initialize\n");
72 fprintf(stderr, "(Typically this happens if you don't have permissions to "
73 "open the device\n");
74 fprintf(stderr, "try re-running as root/Administrator)\n");
76 }
77
79 fprintf(stderr, "No suitable device found. Skipping this test\n");
81 }
82
83 yh_set_verbosity(verbosity);
84
86
87 // Plain commands
88 len = 4;
90 len *= 2;
94 response_len = sizeof(response);
95
96 gettimeofday(&before, NULL);
98 &response_len);
99 gettimeofday(&after, NULL);
100
101 this = (after.tv_sec - before.tv_sec) * 1000;
102 this += ((double) (after.tv_usec - before.tv_usec)) / 1000;
103 if (i == 0) {
106 } else {
109 }
112 }
113 }
114
116
119 fprintf(stderr, "Data mismatch\n");
120 return EXIT_FAILURE;
121 }
122 }
123 }
124
125 // Auth commands
129
133 return EXIT_FAILURE;
134 }
135
137 16, yh_context, &ses);
140 return EXIT_FAILURE;
141 }
142
147 return EXIT_FAILURE;
148 }
149
150 len = 4;
152 len *= 2;
156 response_len = sizeof(response);
157
158 gettimeofday(&before, NULL);
160 &response_len);
161 gettimeofday(&after, NULL);
165 return EXIT_FAILURE;
166 }
167
168 this = (after.tv_sec - before.tv_sec) * 1000;
169 this += ((double) (after.tv_usec - before.tv_usec)) / 1000;
170 if (i == 0) {
173 } else {
176 }
179 }
180 }
181
183
186 fprintf(stderr, "Data mismatch\n");
187 return EXIT_FAILURE;
188 }
189 }
190 }
191
193
195 fprintf(stdout, "| Len | min [ms] | max [ms] | avg [ms] | type |\n");
196 fprintf(stdout, "---------------------------------------------------\n");
199 rs[i].min, rs[i].max, rs[i].tot / N_ITERATIONS);
200 }
203 rs2[i].min, rs2[i].max, rs2[i].tot / N_ITERATIONS);
204 }
205
206 return EXIT_SUCCESS;
207}
Definition yubihsm_shell_tests.c:30
yh_rc yh_create_session(yh_connector *connector, uint16_t authkey_id, const uint8_t *key_enc, size_t key_enc_len, const uint8_t *key_mac, size_t key_mac_len, bool recreate, yh_session **session)
Definition yubihsm.c:616
yh_rc yh_set_verbosity(yh_connector *connector, uint8_t verbosity)
Definition yubihsm.c:3825
yh_rc yh_send_secure_msg(yh_session *session, yh_cmd cmd, const uint8_t *data, size_t data_len, yh_cmd *response_cmd, uint8_t *response, size_t *response_len)
Definition yubihsm.c:416
yh_rc yh_send_plain_msg(yh_connector *connector, yh_cmd cmd, const uint8_t *data, size_t data_len, yh_cmd *response_cmd, uint8_t *response, size_t *response_len)
Definition yubihsm.c:126
memset(pInfo->slotDescription, ' ', 64)
memcpy((char *) pInfo->slotDescription, s, l)
Here is the call graph for this function:
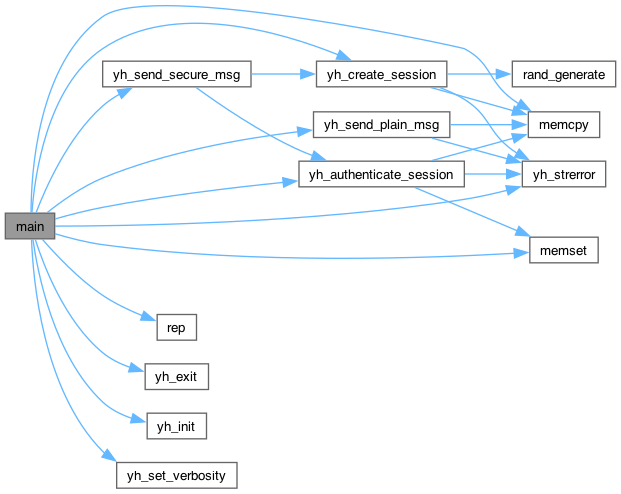
Variable Documentation
◆ devices
| yh_device** devices |
Definition at line 26 of file yubihsm_shell_tests.c.
◆ n_devices
| uint16_t n_devices |
Definition at line 27 of file yubihsm_shell_tests.c.
◆ ses
| yh_session* ses |
Definition at line 28 of file yubihsm_shell_tests.c.