#include <apply_context.hpp>
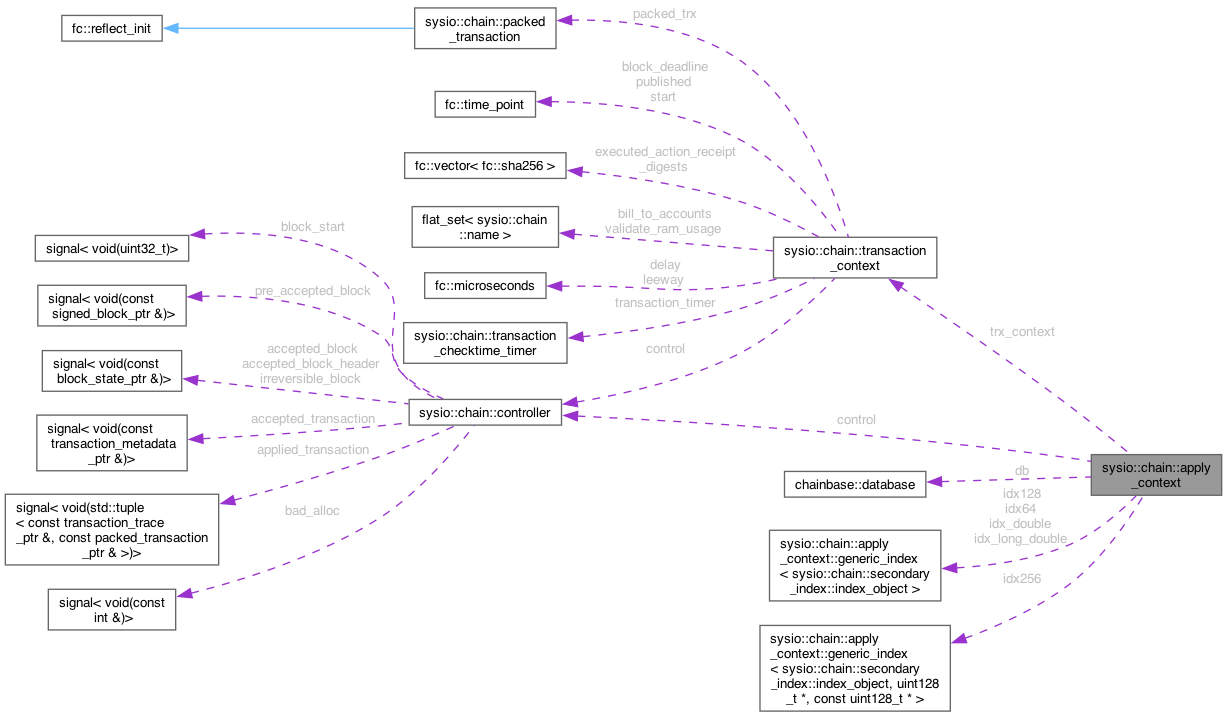
Classes | |
| class | generic_index |
Public Member Functions | |
| apply_context (controller &con, transaction_context &trx_ctx, uint32_t action_ordinal, uint32_t depth=0) | |
| class generic_index | |
| void | exec_one () |
| Execution methods: | |
| void | exec () |
| void | execute_inline (action &&a) |
| void | execute_context_free_inline (action &&a) |
| void | schedule_deferred_transaction (const uint128_t &sender_id, account_name payer, transaction &&trx, bool replace_existing) |
| bool | cancel_deferred_transaction (const uint128_t &sender_id, account_name sender) |
| bool | cancel_deferred_transaction (const uint128_t &sender_id) |
| void | require_authorization (const account_name &account) |
| Authorization methods: | |
| bool | has_authorization (const account_name &account) const |
| void | require_authorization (const account_name &account, const permission_name &permission) |
| bool | is_account (const account_name &account) const |
| exec() | |
| void | get_code_hash (account_name account, uint64_t &code_sequence, fc::sha256 &code_hash, uint8_t &vm_type, uint8_t &vm_version) const |
| void | require_recipient (account_name account) |
| bool | has_recipient (account_name account) const |
| void | console_append (std::string_view val) |
| Console methods: | |
| void | update_db_usage (const account_name &payer, int64_t delta) |
| Database methods: | |
| int | db_store_i64 (name scope, name table, const account_name &payer, uint64_t id, const char *buffer, size_t buffer_size) |
| void | db_update_i64 (int iterator, account_name payer, const char *buffer, size_t buffer_size) |
| void | db_remove_i64 (int iterator) |
| int | db_get_i64 (int iterator, char *buffer, size_t buffer_size) |
| int | db_next_i64 (int iterator, uint64_t &primary) |
| int | db_previous_i64 (int iterator, uint64_t &primary) |
| int | db_find_i64 (name code, name scope, name table, uint64_t id) |
| int | db_lowerbound_i64 (name code, name scope, name table, uint64_t id) |
| int | db_upperbound_i64 (name code, name scope, name table, uint64_t id) |
| int | db_end_i64 (name code, name scope, name table) |
| int | get_action (uint32_t type, uint32_t index, char *buffer, size_t buffer_size) const |
| Misc methods: | |
| int | get_context_free_data (uint32_t index, char *buffer, size_t buffer_size) const |
| vector< account_name > | get_active_producers () const |
| uint64_t | next_global_sequence () |
| uint64_t | next_recv_sequence (const account_metadata_object &receiver_account) |
| uint64_t | next_auth_sequence (account_name actor) |
| void | add_ram_usage (account_name account, int64_t ram_delta) |
| void | finalize_trace (action_trace &trace, const fc::time_point &start) |
| bool | is_context_free () const |
| bool | is_privileged () const |
| action_name | get_receiver () const |
| const action & | get_action () const |
| action_name | get_sender () const |
Public Attributes | |
| controller & | control |
| Fields: | |
| chainbase::database & | db |
| database where state is stored | |
| transaction_context & | trx_context |
| transaction context in which the action is running | |
| std::vector< char > | action_return_value |
| generic_index< index64_object > | idx64 |
| generic_index< index128_object > | idx128 |
| generic_index< index256_object, uint128_t *, const uint128_t * > | idx256 |
| generic_index< index_double_object > | idx_double |
| generic_index< index_long_double_object > | idx_long_double |
Protected Member Functions | |
| uint32_t | schedule_action (uint32_t ordinal_of_action_to_schedule, account_name receiver, bool context_free) |
| uint32_t | schedule_action (action &&act_to_schedule, account_name receiver, bool context_free) |
Detailed Description
Definition at line 18 of file apply_context.hpp.
Constructor & Destructor Documentation
◆ apply_context()
| sysio::chain::apply_context::apply_context | ( | controller & | con, |
| transaction_context & | trx_ctx, | ||
| uint32_t | action_ordinal, | ||
| uint32_t | depth = 0 ) |
Constructor
Definition at line 34 of file apply_context.cpp.
Member Function Documentation
◆ add_ram_usage()
| void sysio::chain::apply_context::add_ram_usage | ( | account_name | account, |
| int64_t | ram_delta ) |
Definition at line 1050 of file apply_context.cpp.
◆ cancel_deferred_transaction() [1/2]
|
inline |
Definition at line 502 of file apply_context.hpp.
◆ cancel_deferred_transaction() [2/2]
| bool sysio::chain::apply_context::cancel_deferred_transaction | ( | const uint128_t & | sender_id, |
| account_name | sender ) |
Definition at line 626 of file apply_context.cpp.
◆ console_append()
|
inline |
Definition at line 547 of file apply_context.hpp.
◆ db_end_i64()
Definition at line 1019 of file apply_context.cpp.
◆ db_find_i64()
Definition at line 973 of file apply_context.cpp.
◆ db_get_i64()
| int sysio::chain::apply_context::db_get_i64 | ( | int | iterator, |
| char * | buffer, | ||
| size_t | buffer_size ) |
Definition at line 914 of file apply_context.cpp.
◆ db_lowerbound_i64()
| int sysio::chain::apply_context::db_lowerbound_i64 | ( | name | code, |
| name | scope, | ||
| name | table, | ||
| uint64_t | id ) |
Definition at line 987 of file apply_context.cpp.

◆ db_next_i64()
| int sysio::chain::apply_context::db_next_i64 | ( | int | iterator, |
| uint64_t & | primary ) |
Definition at line 926 of file apply_context.cpp.
◆ db_previous_i64()
| int sysio::chain::apply_context::db_previous_i64 | ( | int | iterator, |
| uint64_t & | primary ) |
Definition at line 941 of file apply_context.cpp.

◆ db_remove_i64()
| void sysio::chain::apply_context::db_remove_i64 | ( | int | iterator | ) |
Definition at line 878 of file apply_context.cpp.
◆ db_store_i64()
| int sysio::chain::apply_context::db_store_i64 | ( | name | scope, |
| name | table, | ||
| const account_name & | payer, | ||
| uint64_t | id, | ||
| const char * | buffer, | ||
| size_t | buffer_size ) |
Definition at line 778 of file apply_context.cpp.


◆ db_update_i64()
| void sysio::chain::apply_context::db_update_i64 | ( | int | iterator, |
| account_name | payer, | ||
| const char * | buffer, | ||
| size_t | buffer_size ) |
Definition at line 822 of file apply_context.cpp.
◆ db_upperbound_i64()
| int sysio::chain::apply_context::db_upperbound_i64 | ( | name | code, |
| name | scope, | ||
| name | table, | ||
| uint64_t | id ) |
Definition at line 1003 of file apply_context.cpp.

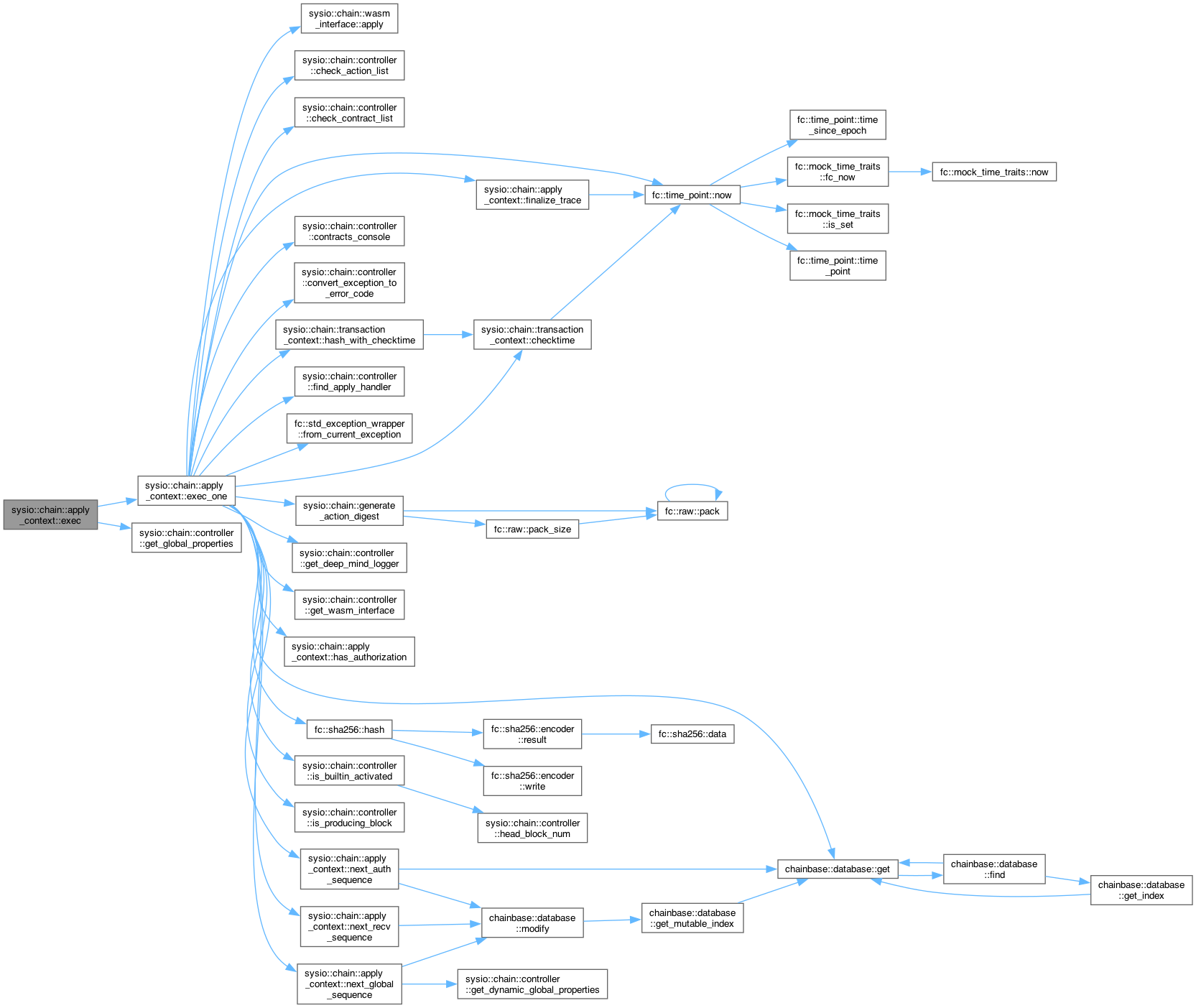
◆ exec()
| void sysio::chain::apply_context::exec | ( | ) |
Definition at line 200 of file apply_context.cpp.
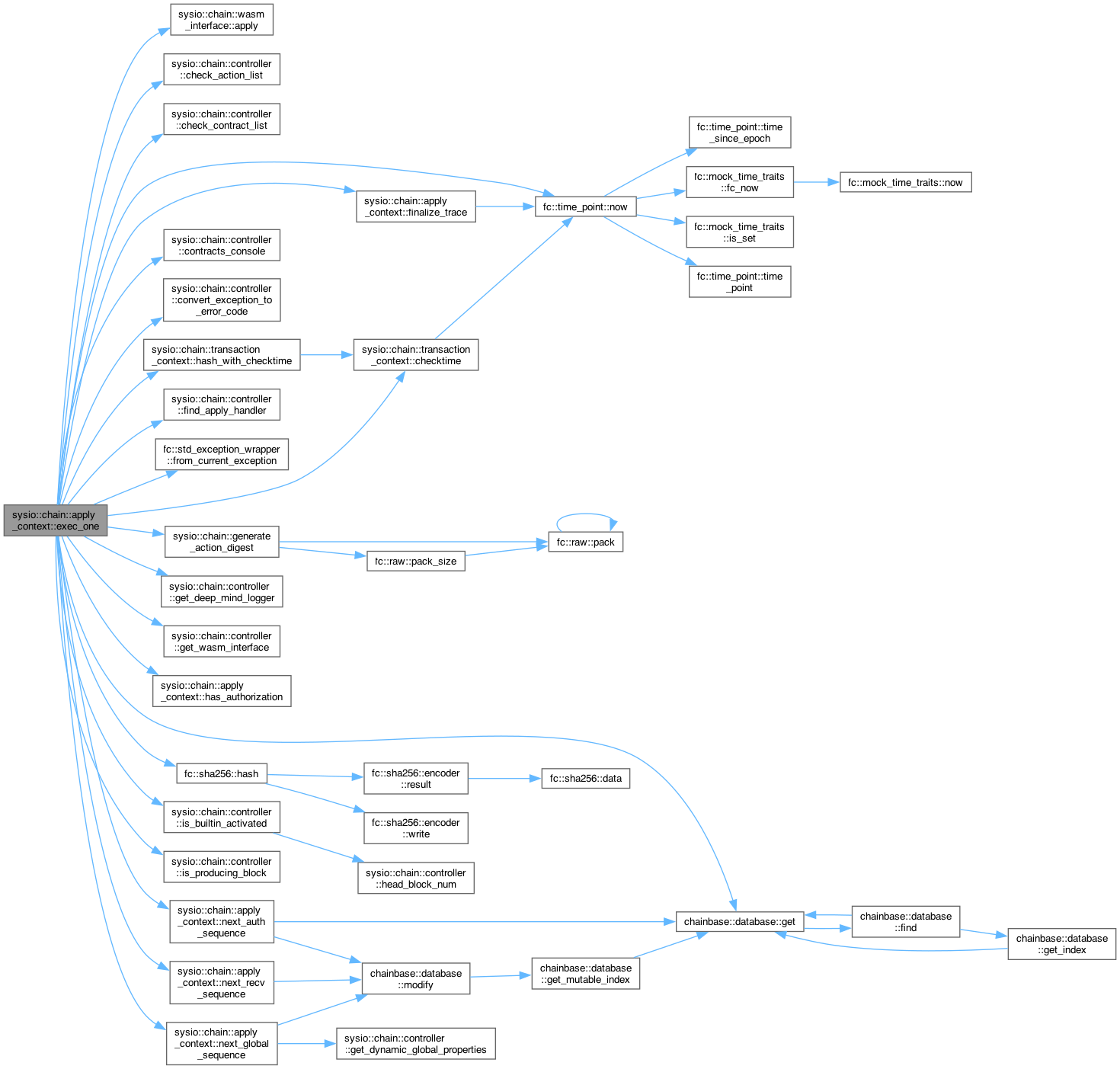
◆ exec_one()
| void sysio::chain::apply_context::exec_one | ( | ) |
Definition at line 53 of file apply_context.cpp.
◆ execute_context_free_inline()
| void sysio::chain::apply_context::execute_context_free_inline | ( | action && | a | ) |
Definition at line 400 of file apply_context.cpp.
◆ execute_inline()
| void sysio::chain::apply_context::execute_inline | ( | action && | a | ) |
This will execute an action after checking the authorization. Inline transactions are implicitly authorized by the current receiver (running code). This method has significant security considerations and several options have been considered:
- privileged accounts (those marked as such by block producers) can authorize any action
- all other actions are only authorized by 'receiver' which means the following: a. the user must set permissions on their account to allow the 'receiver' to act on their behalf
Discarded Implementation: at one point we allowed any account that authorized the current transaction to implicitly authorize an inline transaction. This approach would allow privilege escalation and make it unsafe for users to interact with certain contracts. We opted instead to have applications ask the user for permission to take certain actions rather than making it implicit. This way users can better understand the security risk.
Definition at line 312 of file apply_context.cpp.
◆ finalize_trace()
| void sysio::chain::apply_context::finalize_trace | ( | action_trace & | trace, |
| const fc::time_point & | start ) |
Definition at line 189 of file apply_context.cpp.

◆ get_action() [1/2]
|
inline |
Definition at line 594 of file apply_context.hpp.
◆ get_action() [2/2]
| int sysio::chain::apply_context::get_action | ( | uint32_t | type, |
| uint32_t | index, | ||
| char * | buffer, | ||
| size_t | buffer_size ) const |
Definition at line 737 of file apply_context.cpp.
◆ get_active_producers()
| vector< account_name > sysio::chain::apply_context::get_active_producers | ( | ) | const |
Definition at line 713 of file apply_context.cpp.
◆ get_code_hash()
| void sysio::chain::apply_context::get_code_hash | ( | account_name | account, |
| uint64_t & | code_sequence, | ||
| fc::sha256 & | code_hash, | ||
| uint8_t & | vm_type, | ||
| uint8_t & | vm_version ) const |
Definition at line 228 of file apply_context.cpp.
◆ get_context_free_data()
| int sysio::chain::apply_context::get_context_free_data | ( | uint32_t | index, |
| char * | buffer, | ||
| size_t | buffer_size ) const |
Definition at line 763 of file apply_context.cpp.
◆ get_receiver()
|
inline |
Definition at line 593 of file apply_context.hpp.
◆ get_sender()
| action_name sysio::chain::apply_context::get_sender | ( | ) | const |
Definition at line 1059 of file apply_context.cpp.
◆ has_authorization()
| bool sysio::chain::apply_context::has_authorization | ( | const account_name & | account | ) | const |
Definition at line 257 of file apply_context.cpp.
◆ has_recipient()
| bool sysio::chain::apply_context::has_recipient | ( | account_name | account | ) | const |
Return true if the current action has already been scheduled to be delivered to the specified account.
Definition at line 276 of file apply_context.cpp.

◆ is_account()
| bool sysio::chain::apply_context::is_account | ( | const account_name & | account | ) | const |
- Returns
- true if account exists, false if it does not
Definition at line 224 of file apply_context.cpp.
◆ is_context_free()
|
inline |
Definition at line 591 of file apply_context.hpp.
◆ is_privileged()
|
inline |
Definition at line 592 of file apply_context.hpp.
◆ next_auth_sequence()
| uint64_t sysio::chain::apply_context::next_auth_sequence | ( | account_name | actor | ) |
Definition at line 1042 of file apply_context.cpp.

◆ next_global_sequence()
| uint64_t sysio::chain::apply_context::next_global_sequence | ( | ) |
Definition at line 1028 of file apply_context.cpp.
◆ next_recv_sequence()
| uint64_t sysio::chain::apply_context::next_recv_sequence | ( | const account_metadata_object & | receiver_account | ) |
Definition at line 1036 of file apply_context.cpp.

◆ require_authorization() [1/2]
| void sysio::chain::apply_context::require_authorization | ( | const account_name & | account | ) |
Require account to have approved of this message
- Parameters
-
account The account whose approval is required
This method will check that account is listed in the message's declared authorizations, and marks the authorization as used. Note that all authorizations on a message must be used, or the message is invalid.
- Exceptions
-
missing_auth_exception If no sufficient permission was found
Definition at line 248 of file apply_context.cpp.
◆ require_authorization() [2/2]
| void sysio::chain::apply_context::require_authorization | ( | const account_name & | account, |
| const permission_name & | permission ) |
Definition at line 264 of file apply_context.cpp.
◆ require_recipient()
| void sysio::chain::apply_context::require_recipient | ( | account_name | account | ) |
Requires that the current action be delivered to account
Definition at line 283 of file apply_context.cpp.
◆ schedule_action() [1/2]
|
protected |
Definition at line 651 of file apply_context.cpp.
◆ schedule_action() [2/2]
|
protected |
Definition at line 641 of file apply_context.cpp.
◆ schedule_deferred_transaction()
| void sysio::chain::apply_context::schedule_deferred_transaction | ( | const uint128_t & | sender_id, |
| account_name | payer, | ||
| transaction && | trx, | ||
| bool | replace_existing ) |
uses payer's storage
Definition at line 426 of file apply_context.cpp.
◆ update_db_usage()
| void sysio::chain::apply_context::update_db_usage | ( | const account_name & | payer, |
| int64_t | delta ) |
Definition at line 723 of file apply_context.cpp.
Member Data Documentation
◆ action_return_value
| std::vector<char> sysio::chain::apply_context::action_return_value |
Definition at line 616 of file apply_context.hpp.
◆ control
| controller& sysio::chain::apply_context::control |
Definition at line 601 of file apply_context.hpp.
◆ db
| chainbase::database& sysio::chain::apply_context::db |
Definition at line 602 of file apply_context.hpp.
◆ idx128
| generic_index<index128_object> sysio::chain::apply_context::idx128 |
Definition at line 618 of file apply_context.hpp.
◆ idx256
| generic_index<index256_object, uint128_t*, const uint128_t*> sysio::chain::apply_context::idx256 |
Definition at line 619 of file apply_context.hpp.
◆ idx64
| generic_index<index64_object> sysio::chain::apply_context::idx64 |
Definition at line 617 of file apply_context.hpp.
◆ idx_double
| generic_index<index_double_object> sysio::chain::apply_context::idx_double |
Definition at line 620 of file apply_context.hpp.
◆ idx_long_double
| generic_index<index_long_double_object> sysio::chain::apply_context::idx_long_double |
Definition at line 621 of file apply_context.hpp.
◆ trx_context
| transaction_context& sysio::chain::apply_context::trx_context |
Definition at line 603 of file apply_context.hpp.
The documentation for this class was generated from the following files:
- libraries/chain/include/sysio/chain/apply_context.hpp
- libraries/chain/apply_context.cpp