#include <authorization_manager.hpp>
Public Types | |
| using | permission_id_type = permission_object::id_type |
Public Member Functions | |
| authorization_manager (controller &c, chainbase::database &d) | |
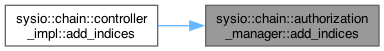
| void | add_indices () |
| void | initialize_database () |
| void | add_to_snapshot (const snapshot_writer_ptr &snapshot) const |
| void | read_from_snapshot (const snapshot_reader_ptr &snapshot) |
| const permission_object & | create_permission (account_name account, permission_name name, permission_id_type parent, const authority &auth, time_point initial_creation_time=time_point()) |
| const permission_object & | create_permission (account_name account, permission_name name, permission_id_type parent, authority &&auth, time_point initial_creation_time=time_point()) |
| void | modify_permission (const permission_object &permission, const authority &auth) |
| void | remove_permission (const permission_object &permission) |
| void | update_permission_usage (const permission_object &permission) |
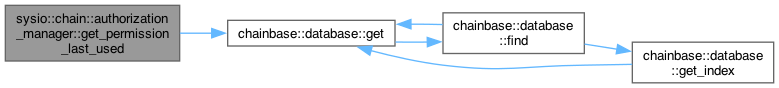
| fc::time_point | get_permission_last_used (const permission_object &permission) const |
| const permission_object * | find_permission (const permission_level &level) const |
| const permission_object & | get_permission (const permission_level &level) const |
| std::optional< permission_name > | lookup_minimum_permission (account_name authorizer_account, scope_name code_account, action_name type) const |
| Find the lowest authority level required for authorizer_account to authorize a message of the specified type. | |
| void | check_authorization (const vector< action > &actions, const flat_set< public_key_type > &provided_keys, const flat_set< permission_level > &provided_permissions=flat_set< permission_level >(), fc::microseconds provided_delay=fc::microseconds(0), const std::function< void()> &checktime=std::function< void()>(), bool allow_unused_keys=false, bool check_but_dont_fail=false, const flat_set< permission_level > &satisfied_authorizations=flat_set< permission_level >()) const |
| Check authorizations of a vector of actions with provided keys, permission levels, and delay. | |
| void | check_authorization (account_name account, permission_name permission, const flat_set< public_key_type > &provided_keys, const flat_set< permission_level > &provided_permissions=flat_set< permission_level >(), fc::microseconds provided_delay=fc::microseconds(0), const std::function< void()> &checktime=std::function< void()>(), bool allow_unused_keys=false) const |
| Check authorizations of a permission with provided keys, permission levels, and delay. | |
| flat_set< public_key_type > | get_required_keys (const transaction &trx, const flat_set< public_key_type > &candidate_keys, fc::microseconds provided_delay=fc::microseconds(0)) const |
Static Public Attributes | |
| static std::function< void()> | _noop_checktime {&noop_checktime} |
Detailed Description
Definition at line 19 of file authorization_manager.hpp.
Member Typedef Documentation
◆ permission_id_type
Definition at line 21 of file authorization_manager.hpp.
Constructor & Destructor Documentation
◆ authorization_manager()
|
explicit |
Definition at line 24 of file authorization_manager.cpp.
Member Function Documentation
◆ add_indices()
| void sysio::chain::authorization_manager::add_indices | ( | ) |
Definition at line 27 of file authorization_manager.cpp.
◆ add_to_snapshot()
| void sysio::chain::authorization_manager::add_to_snapshot | ( | const snapshot_writer_ptr & | snapshot | ) | const |
Definition at line 96 of file authorization_manager.cpp.

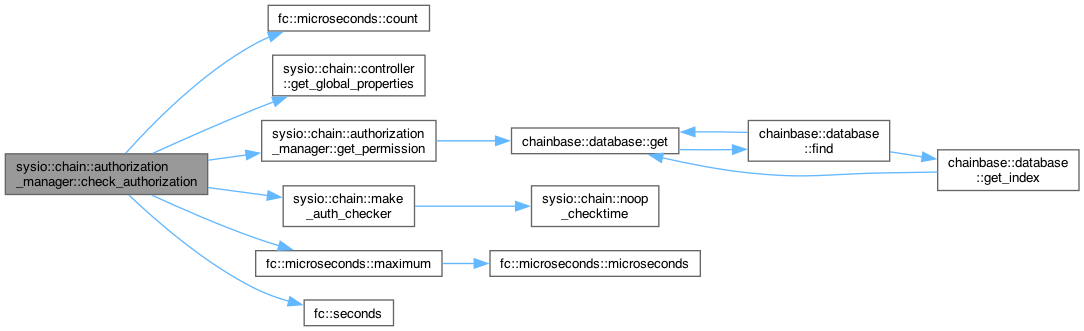
◆ check_authorization() [1/2]
| void sysio::chain::authorization_manager::check_authorization | ( | account_name | account, |
| permission_name | permission, | ||
| const flat_set< public_key_type > & | provided_keys, | ||
| const flat_set< permission_level > & | provided_permissions = flat_set<permission_level>(), | ||
| fc::microseconds | provided_delay = fc::microseconds(0), | ||
| const std::function< void()> & | checktime = std::function<void()>(), | ||
| bool | allow_unused_keys = false ) const |
- Parameters
-
account - the account owner of the permission permission - the permission name to check for authorization provided_keys - a set of public keys provided_permissions - the set of permissions which can be considered satisfied (empty permission name acts as wildcard) provided_delay - the delay considered to be satisfied for the authorization check checktime - the function that can be called to track CPU usage and time during the process of checking authorization allow_unused_keys - true if method does not require all keys to be used
Definition at line 575 of file authorization_manager.cpp.
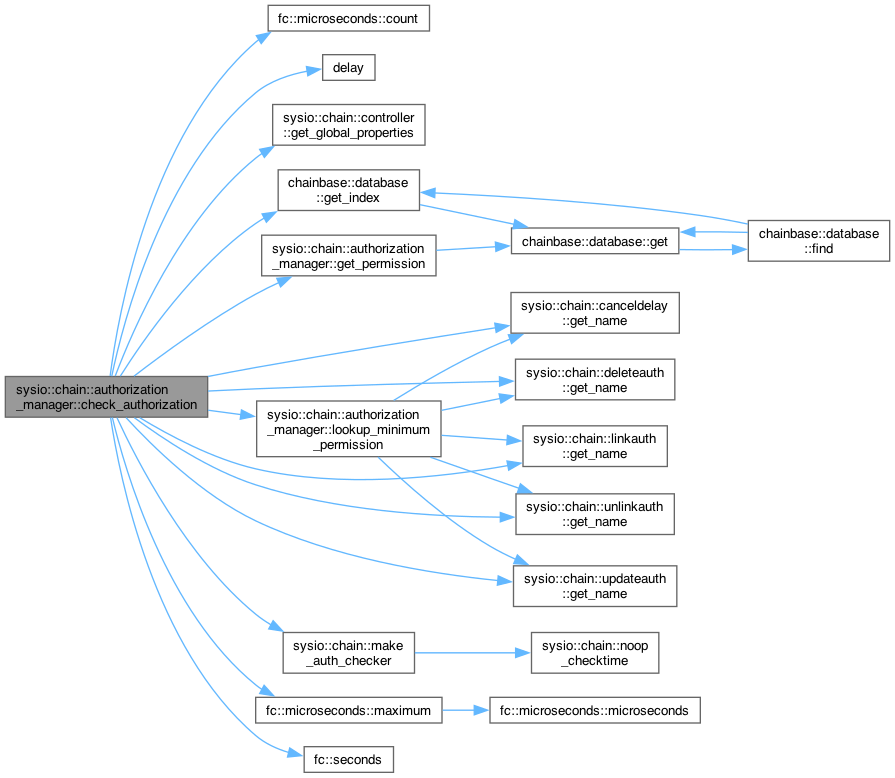
◆ check_authorization() [2/2]
| void sysio::chain::authorization_manager::check_authorization | ( | const vector< action > & | actions, |
| const flat_set< public_key_type > & | provided_keys, | ||
| const flat_set< permission_level > & | provided_permissions = flat_set<permission_level>(), | ||
| fc::microseconds | provided_delay = fc::microseconds(0), | ||
| const std::function< void()> & | checktime = std::function<void()>(), | ||
| bool | allow_unused_keys = false, | ||
| bool | check_but_dont_fail = false, | ||
| const flat_set< permission_level > & | satisfied_authorizations = flat_set<permission_level>() ) const |
- Parameters
-
actions - the actions to check authorization across provided_keys - the set of public keys which have authorized the transaction provided_permissions - the set of permissions which have authorized the transaction (empty permission name acts as wildcard) provided_delay - the delay satisfied by the transaction checktime - the function that can be called to track CPU usage and time during the process of checking authorization allow_unused_keys - true if method should not assert on unused keys
Definition at line 471 of file authorization_manager.cpp.
◆ create_permission() [1/2]
| const permission_object & sysio::chain::authorization_manager::create_permission | ( | account_name | account, |
| permission_name | name, | ||
| permission_id_type | parent, | ||
| authority && | auth, | ||
| time_point | initial_creation_time = time_point() ) |
Definition at line 168 of file authorization_manager.cpp.
◆ create_permission() [2/2]
| const permission_object & sysio::chain::authorization_manager::create_permission | ( | account_name | account, |
| permission_name | name, | ||
| permission_id_type | parent, | ||
| const authority & | auth, | ||
| time_point | initial_creation_time = time_point() ) |
Definition at line 133 of file authorization_manager.cpp.

◆ find_permission()
| const permission_object * sysio::chain::authorization_manager::find_permission | ( | const permission_level & | level | ) | const |
Definition at line 251 of file authorization_manager.cpp.
◆ get_permission()
| const permission_object & sysio::chain::authorization_manager::get_permission | ( | const permission_level & | level | ) | const |
Definition at line 257 of file authorization_manager.cpp.
◆ get_permission_last_used()
| fc::time_point sysio::chain::authorization_manager::get_permission_last_used | ( | const permission_object & | permission | ) | const |
◆ get_required_keys()
| flat_set< public_key_type > sysio::chain::authorization_manager::get_required_keys | ( | const transaction & | trx, |
| const flat_set< public_key_type > & | candidate_keys, | ||
| fc::microseconds | provided_delay = fc::microseconds(0) ) const |
Definition at line 614 of file authorization_manager.cpp.
◆ initialize_database()
| void sysio::chain::authorization_manager::initialize_database | ( | ) |
reserve perm 0 (used else where)
Definition at line 31 of file authorization_manager.cpp.


◆ lookup_minimum_permission()
| std::optional< permission_name > sysio::chain::authorization_manager::lookup_minimum_permission | ( | account_name | authorizer_account, |
| scope_name | code_account, | ||
| action_name | type ) const |
- Parameters
-
authorizer_account The account authorizing the message code_account The account which publishes the contract that handles the message type The type of message
Definition at line 286 of file authorization_manager.cpp.
◆ modify_permission()
| void sysio::chain::authorization_manager::modify_permission | ( | const permission_object & | permission, |
| const authority & | auth ) |
Definition at line 203 of file authorization_manager.cpp.
◆ read_from_snapshot()
| void sysio::chain::authorization_manager::read_from_snapshot | ( | const snapshot_reader_ptr & | snapshot | ) |
Definition at line 113 of file authorization_manager.cpp.

◆ remove_permission()
| void sysio::chain::authorization_manager::remove_permission | ( | const permission_object & | permission | ) |
Definition at line 225 of file authorization_manager.cpp.
◆ update_permission_usage()
| void sysio::chain::authorization_manager::update_permission_usage | ( | const permission_object & | permission | ) |
Definition at line 240 of file authorization_manager.cpp.
Member Data Documentation
◆ _noop_checktime
|
static |
Definition at line 116 of file authorization_manager.hpp.
The documentation for this class was generated from the following files:
- libraries/chain/include/sysio/chain/authorization_manager.hpp
- libraries/chain/authorization_manager.cpp