Loading...
Searching...
No Matches
util.h File Reference
#include <openssl/bn.h>#include <openssl/evp.h>#include <stdbool.h>#include <stdint.h>#include <yubihsm.h>
Include dependency graph for util.h:
This graph shows which files directly or indirectly include this file:
Go to the source code of this file.
Macros | |
| #define | YH_INTERNAL __attribute__((visibility("hidden"))) |
Enumerations | |
| enum | format_t { _base64 , _binary , _hex } |
Functions | |
| bool YH_INTERNAL | set_component (uint8_t *in_ptr, const BIGNUM *bn, int32_t element_len) |
| bool YH_INTERNAL | read_private_key (uint8_t *buf, size_t len, yh_algorithm *algo, uint8_t *bytes, size_t *bytes_len, bool internal_repr) |
| void YH_INTERNAL | format_digest (uint8_t *digest, char *str, uint16_t len) |
| int YH_INTERNAL | algo2nid (yh_algorithm algo) |
| bool YH_INTERNAL | algo2type (yh_algorithm algorithm, yh_object_type *type) |
| void YH_INTERNAL | parse_NID (uint8_t *data, uint16_t data_len, const EVP_MD **md_type, int *digestinfo_len) |
| bool YH_INTERNAL | read_file (FILE *fp, uint8_t *buf, size_t *buf_len) |
| bool YH_INTERNAL | write_file (const uint8_t *buf, size_t buf_len, FILE *fp, format_t format) |
| bool YH_INTERNAL | read_ed25519_key (uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len) |
| bool YH_INTERNAL | write_ed25519_key (uint8_t *buf, size_t buf_len, FILE *fp, bool b64_encode) |
| bool YH_INTERNAL | base64_decode (const char *in, uint8_t *out, size_t *len) |
| bool YH_INTERNAL | hex_decode (const char *in, uint8_t *out, size_t *len) |
| bool YH_INTERNAL | split_hmac_key (yh_algorithm algorithm, uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len) |
Macro Definition Documentation
◆ YH_INTERNAL
Enumeration Type Documentation
◆ format_t
| enum format_t |
Function Documentation
◆ algo2nid()
| int YH_INTERNAL algo2nid | ( | yh_algorithm | algo | ) |
Definition at line 335 of file util.c.
335 {
336 switch (algo) {
338 return NID_X9_62_prime256v1;
339
341 return NID_secp384r1;
342
344 return NID_secp521r1;
345
347 return NID_secp224r1;
348
350 return NID_secp256k1;
351
352#ifdef NID_brainpoolP256r1
354 return NID_brainpoolP256r1;
355#endif
356
357#ifdef NID_brainpoolP384r1
359 return NID_brainpoolP384r1;
360#endif
361
362#ifdef NID_brainpoolP512r1
364 return NID_brainpoolP512r1;
365#endif
366
367 default:
368 return 0;
369 }
370
371 return 0;
372}
Here is the caller graph for this function:
◆ algo2type()
| bool YH_INTERNAL algo2type | ( | yh_algorithm | algorithm, |
| yh_object_type * | type ) |
Definition at line 374 of file util.c.
374 {
375
406 *type = YH_ASYMMETRIC_KEY;
407 break;
408
413 *type = YH_HMAC_KEY;
414 break;
415
419 *type = YH_WRAP_KEY;
420 break;
421
424 *type = YH_OPAQUE;
425 break;
426
428 *type = YH_TEMPLATE;
429 break;
430
434 *type = YH_OTP_AEAD_KEY;
435 break;
436
438 *type = YH_AUTHENTICATION_KEY;
439 break;
440
445 default:
446 return false;
447 }
448
449 return true;
450}
@ YH_OTP_AEAD_KEY
OTP AEAD Key is a secret key used to decrypt Yubico OTP values.
Definition yubihsm.h:376
@ YH_HMAC_KEY
HMAC Key is a secret key used when computing and verifying HMAC signatures.
Definition yubihsm.h:371
@ YH_ASYMMETRIC_KEY
Asymmetric Key is the private key of an asymmetric key-pair.
Definition yubihsm.h:366
@ YH_AUTHENTICATION_KEY
Authentication Key is used to establish Sessions with a device.
Definition yubihsm.h:364
Here is the caller graph for this function:
◆ base64_decode()
| bool YH_INTERNAL base64_decode | ( | const char * | in, |
| uint8_t * | out, | ||
| size_t * | len ) |
Definition at line 503 of file util.c.
503 {
505 BIO *b64 = BIO_new(BIO_f_base64());
506 BIO *bio = BIO_new(BIO_s_mem());
507 BIO_set_flags(b64, BIO_FLAGS_BASE64_NO_NL);
508 BIO_push(b64, bio);
509
510 (void) BIO_write(bio, in, strlen(in));
511 (void) BIO_flush(bio);
513
514 BIO_free_all(b64);
515
517 return false;
518 } else {
520 return true;
521 }
522}
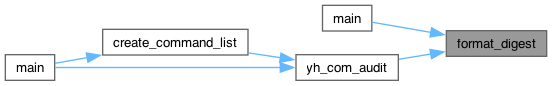
◆ format_digest()
| void YH_INTERNAL format_digest | ( | uint8_t * | digest, |
| char * | str, | ||
| uint16_t | len ) |
◆ hex_decode()
| bool YH_INTERNAL hex_decode | ( | const char * | in, |
| uint8_t * | out, | ||
| size_t * | len ) |
Definition at line 524 of file util.c.
524 {
525 int pos = 0;
528 in_len--;
529 }
531 in_len--;
532 }
534 return false;
536 return false;
537 }
538
540 char *endptr = NULL;
543 errno = 0;
544
545 buf[0] = in[pos];
546 buf[1] = in[pos + 1];
548 if ((errno == ERANGE && (num < 0 || num > UCHAR_MAX)) ||
549 (errno != 0 && num == 0) || *endptr != '\0') {
550 return false;
551 }
552 out[i] = (uint8_t) num;
553 pos += 2;
554 }
556 return true;
557}
@ num
Here is the caller graph for this function:

◆ parse_NID()
| void YH_INTERNAL parse_NID | ( | uint8_t * | data, |
| uint16_t | data_len, | ||
| const EVP_MD ** | md_type, | ||
| int * | digestinfo_len ) |
Definition at line 452 of file util.c.
453 {
454 if (data_len >= sizeof(sha1oid) &&
455 memcmp(sha1oid, data, sizeof(sha1oid)) == 0) {
456 *md_type = EVP_sha1();
457 *digestinfo_len = sizeof(sha1oid);
458 } else if (data_len >= sizeof(sha256oid) &&
459 memcmp(sha256oid, data, sizeof(sha256oid)) == 0) {
460 *md_type = EVP_sha256();
461 *digestinfo_len = sizeof(sha256oid);
462 } else if (data_len >= sizeof(sha384oid) &&
463 memcmp(sha384oid, data, sizeof(sha384oid)) == 0) {
464 *md_type = EVP_sha384();
465 *digestinfo_len = sizeof(sha384oid);
466 } else if (data_len >= sizeof(sha512oid) &&
467 memcmp(sha512oid, data, sizeof(sha512oid)) == 0) {
468 *md_type = EVP_sha512();
469 *digestinfo_len = sizeof(sha512oid);
470 } else {
471 *md_type = EVP_md_null();
472 *digestinfo_len = 0;
473 }
474}
Here is the caller graph for this function:
◆ read_ed25519_key()
| bool YH_INTERNAL read_ed25519_key | ( | uint8_t * | in, |
| size_t | in_len, | ||
| uint8_t * | out, | ||
| size_t * | out_len ) |
Definition at line 77 of file util.c.
78 {
79
80 uint8_t decoded[128];
81 size_t decoded_len = sizeof(decoded);
82
83 if (memcmp(in, PEM_private_header, 28) != 0 ||
84 memcmp(in + in_len - 26, PEM_private_trailer, 25) != 0) {
85 return false;
86 }
87
89 BIO *b64 = BIO_new(BIO_f_base64());
90 BIO *bio = BIO_new(BIO_s_mem());
91 BIO_set_flags(b64, BIO_FLAGS_BASE64_NO_NL);
92 BIO_push(b64, bio);
93
94 (void) BIO_write(bio, in + 28, in_len - 28 - 25);
95 (void) BIO_flush(bio);
96 ret = BIO_read(b64, decoded, decoded_len);
97
98 BIO_free_all(b64);
99
101 return false;
102 }
103
104 if (memcmp(decoded, ed25519private_oid, sizeof(ed25519private_oid)) != 0) {
105 return false;
106 }
107
108 memcpy(out, decoded + 16, 32);
109 *out_len = 32;
110
111 insecure_memzero(decoded, 48);
112
113 return true;
114}
memcpy((char *) pInfo->slotDescription, s, l)
Here is the call graph for this function:
Here is the caller graph for this function:
◆ read_file()
| bool YH_INTERNAL read_file | ( | FILE * | fp, |
| uint8_t * | buf, | ||
| size_t * | buf_len ) |
Definition at line 476 of file util.c.
476 {
477 size_t n = 0;
478 size_t available = *buf_len;
480
481 do {
482 n = fread(p, 1, available, fp);
483 available -= n;
484 p += n;
485 } while (!feof(fp) && !ferror(fp) && available > 0);
486
487 if (ferror(fp)) {
488 return false;
489 }
490
491 if (!feof(fp) && available == 0) {
492 uint8_t b[1];
493 n = fread(b, 1, 1, fp);
494 if (!feof(fp)) {
495 return false;
496 }
497 }
498
500 return true;
501}
Here is the caller graph for this function:
◆ read_private_key()
| bool YH_INTERNAL read_private_key | ( | uint8_t * | buf, |
| size_t | len, | ||
| yh_algorithm * | algo, | ||
| uint8_t * | bytes, | ||
| size_t * | bytes_len, | ||
| bool | internal_repr ) |
Definition at line 116 of file util.c.
117 {
118
120 *algo = YH_ALGO_EC_ED25519;
121 return true;
122 }
123
124 EVP_PKEY *private_key;
125
126 BIO *bio = BIO_new(BIO_s_mem());
127 if (bio == NULL) {
128 return false;
129 }
130
132
133 private_key = PEM_read_bio_PrivateKey(bio, NULL, NULL, /*password*/ NULL);
134 BIO_free_all(bio);
135 if (private_key == NULL) {
136 return false;
137 }
138
140
141 RSA *rsa = NULL;
142
143 BIGNUM *x = NULL;
145 EC_KEY *ec_private = NULL;
146
147 switch (EVP_PKEY_base_id(private_key)) {
148 case EVP_PKEY_RSA: {
149 rsa = EVP_PKEY_get1_RSA(private_key);
150 unsigned char e[4];
151 int size = RSA_size(rsa);
153
154 RSA_get0_key(rsa, &bn_n, &bn_e, NULL);
155 RSA_get0_factors(rsa, &bn_p, &bn_q);
156
158 !(e[0] == 0x01 && e[1] == 0x00 && e[2] == 0x01)) {
159 goto cleanup;
160 }
161
162 if (size == 256) {
163 *algo = YH_ALGO_RSA_2048;
164 } else if (size == 384) {
165 *algo = YH_ALGO_RSA_3072;
166 } else if (size == 512) {
167 *algo = YH_ALGO_RSA_4096;
168 } else {
169 goto cleanup;
170 }
171
173 goto cleanup;
174 }
175
177 goto cleanup;
178 }
179
180 if (internal_repr == true) {
183
184 RSA_get0_crt_params(rsa, &dmp1, &dmq1, &iqmp);
186 goto cleanup;
187 }
188 ptr += size / 2;
189
191 goto cleanup;
192 }
193 ptr += size / 2;
194
196 goto cleanup;
197 }
198 ptr += size / 2;
199
201 goto cleanup;
202 }
203
204 *bytes_len = (size / 2) * 7;
205 } else {
206 *bytes_len = size;
207 }
208 } break;
209
210 case EVP_PKEY_EC: {
211 ec_private = EVP_PKEY_get1_EC_KEY(private_key);
212 if (ec_private == NULL) {
213 goto cleanup;
214 }
215
217 const EC_GROUP *group = EC_KEY_get0_group(ec_private);
218 int curve = EC_GROUP_get_curve_name(group);
219 int size = 0;
220
221 if (curve == NID_X9_62_prime256v1) {
222 *algo = YH_ALGO_EC_P256;
223 size = 32;
224 } else if (curve == NID_secp384r1) {
225 *algo = YH_ALGO_EC_P384;
226 size = 48;
227 } else if (curve == NID_secp521r1) {
228 *algo = YH_ALGO_EC_P521;
229 size = 66;
230 } else if (curve == NID_secp224r1) {
231 *algo = YH_ALGO_EC_P224;
232 size = 28;
233#ifdef NID_brainpoolP256r1
234 } else if (curve == NID_brainpoolP256r1) {
235 *algo = YH_ALGO_EC_BP256;
236 size = 32;
237#endif
238#ifdef NID_brainpoolP384r1
239 } else if (curve == NID_brainpoolP384r1) {
240 *algo = YH_ALGO_EC_BP384;
241 size = 48;
242#endif
243#ifdef NID_brainpoolP512r1
244 } else if (curve == NID_brainpoolP512r1) {
245 *algo = YH_ALGO_EC_BP512;
246 size = 64;
247#endif
248 } else if (curve == NID_secp256k1) {
249 *algo = YH_ALGO_EC_K256;
250 size = 32;
251 } else {
252 goto cleanup;
253 }
254
256 goto cleanup;
257 }
258
259 if (internal_repr == true) {
260 const EC_POINT *ec_public = EC_KEY_get0_public_key(ec_private);
261
262 x = BN_new();
263 if (x == NULL) {
264 goto cleanup;
265 }
266
267 y = BN_new();
268 if (y == NULL) {
269 goto cleanup;
270 }
271
272 if (EC_POINT_get_affine_coordinates_GFp(group, ec_public, x, y, NULL) ==
273 0) {
274 goto cleanup;
275 }
276
279 goto cleanup;
280 }
281 ptr += size;
282
284 goto cleanup;
285 }
286
287 *bytes_len = size * 3;
288 } else {
289 *bytes_len = size;
290 }
291 } break;
292
293 default:
294 goto cleanup;
295 }
296
298
299cleanup:
300
301 if (rsa != NULL) {
302 RSA_free(rsa);
303 rsa = NULL;
304 }
305
306 if (x != NULL) {
307 BN_free(x);
308 x = NULL;
309 }
310
311 if (y != NULL) {
312 BN_free(y);
313 y = NULL;
314 }
315
316 if (ec_private != NULL) {
317 EC_KEY_free(ec_private);
318 ec_private = NULL;
319 }
320
321 EVP_PKEY_free(private_key);
322
324}
void RSA_get0_crt_params(const RSA *r, const BIGNUM **dmp1, const BIGNUM **dmq1, const BIGNUM **iqmp)
Definition openssl-compat.c:54
void RSA_get0_key(const RSA *r, const BIGNUM **n, const BIGNUM **e, const BIGNUM **d)
Definition openssl-compat.c:37
void RSA_get0_factors(const RSA *r, const BIGNUM **p, const BIGNUM **q)
Definition openssl-compat.c:47
bool read_ed25519_key(uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
Definition util.c:77
bool set_component(unsigned char *in_ptr, const BIGNUM *bn, int element_len)
Definition util.c:30
Here is the call graph for this function:
Here is the caller graph for this function:
◆ set_component()
| bool YH_INTERNAL set_component | ( | uint8_t * | in_ptr, |
| const BIGNUM * | bn, | ||
| int32_t | element_len ) |
◆ split_hmac_key()
| bool YH_INTERNAL split_hmac_key | ( | yh_algorithm | algorithm, |
| uint8_t * | in, | ||
| size_t | in_len, | ||
| uint8_t * | out, | ||
| size_t * | out_len ) |
Definition at line 653 of file util.c.
654 {
655
656 uint8_t key[128 * 2] = {0};
657 uint8_t block_size;
658
661 block_size = EVP_MD_block_size(EVP_sha1());
662 break;
663
665 block_size = EVP_MD_block_size(EVP_sha256());
666 break;
667
669 block_size = EVP_MD_block_size(EVP_sha384());
670 break;
671
673 block_size = EVP_MD_block_size(EVP_sha512());
674 break;
675
676 default:
677 return false;
678 }
679
681 return false; // TODO(adma): hash the key
682 }
683
685
687 out[i] = key[i] ^ 0x36;
688 out[i + block_size] = key[i] ^ 0x5c;
689 }
690
691 *out_len = 2 * block_size;
692
693 return true;
694}
Here is the call graph for this function:
Here is the caller graph for this function:

◆ write_ed25519_key()
| bool YH_INTERNAL write_ed25519_key | ( | uint8_t * | buf, |
| size_t | buf_len, | ||
| FILE * | fp, | ||
| bool | b64_encode ) |
Definition at line 622 of file util.c.
623 {
624
625 if (b64_encode == true) {
627 uint8_t asn1[64];
628 uint8_t padding = 0;
629
631 padding = 1;
632 }
633
635 asn1[1] += padding;
637 asn1[10] += padding;
639
641 false);
645 fp, false);
646 } else {
648 }
649
650 return true;
651}
bool write_file(const uint8_t *buf, size_t buf_len, FILE *fp, format_t format)
Definition util.c:559
memset(pInfo->slotDescription, ' ', 64)
Here is the call graph for this function:
Here is the caller graph for this function:

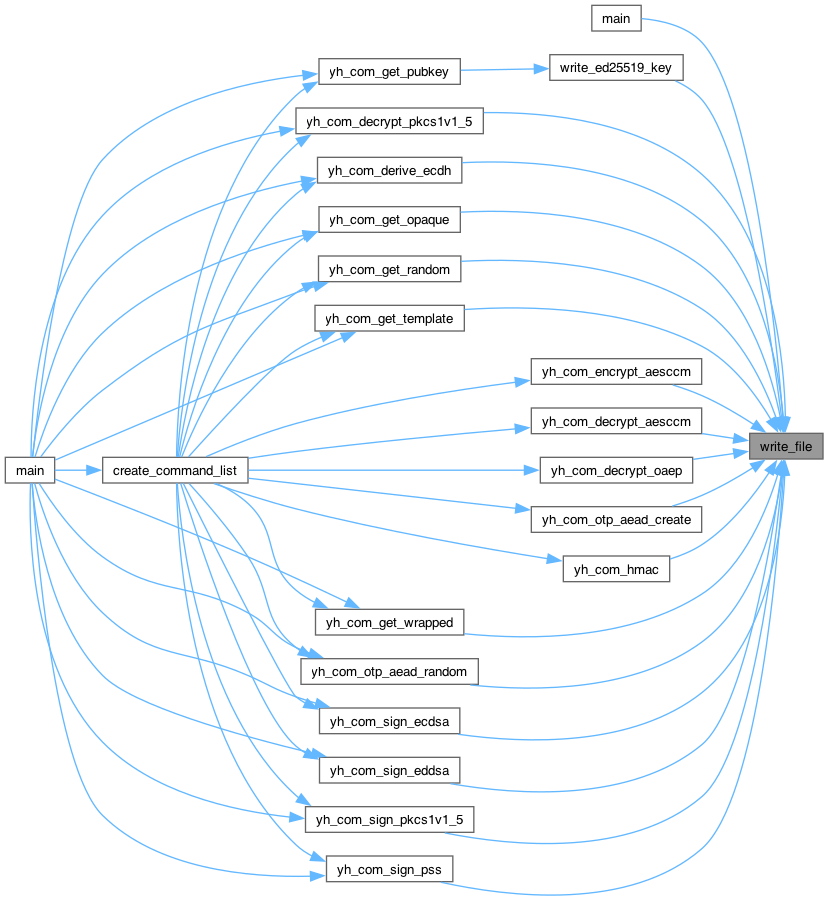
◆ write_file()
| bool YH_INTERNAL write_file | ( | const uint8_t * | buf, |
| size_t | buf_len, | ||
| FILE * | fp, | ||
| format_t | format ) |
Definition at line 559 of file util.c.
559 {
560
562 uint8_t *data = NULL;
563 size_t length = buf_len;
564 size_t written = 0;
565 BIO *b64 = NULL;
566
568 BIO *bio;
569 BUF_MEM *bufferPtr;
570
571 b64 = BIO_new(BIO_f_base64());
572 bio = BIO_new(BIO_s_mem());
573 bio = BIO_push(b64, bio);
574
575 (void) BIO_set_flags(bio, BIO_FLAGS_BASE64_NO_NL);
576 (void) BIO_write(bio, buf, buf_len);
577 (void) BIO_flush(bio);
578 (void) BIO_get_mem_ptr(bio, &bufferPtr);
580 length = bufferPtr->length;
582 data = calloc(buf_len * 2 + 1, 1);
583 if (data == NULL) {
584 return false;
585 }
586 for (size_t i = 0; i < buf_len; i++) {
588 }
589 p = data;
590 length = buf_len * 2;
591 }
592
593 do {
594 written = fwrite(p, 1, length, fp);
595 length -= written;
596 p += written;
597 } while (!feof(fp) && !ferror(fp) && length > 0);
598
599 if (fp == stdout || fp == stderr) {
600 fprintf(fp, "\n");
601 }
602
603 if (b64 != NULL) {
604 BIO_free_all(b64);
605 b64 = NULL;
606 }
607
608 if (data != NULL) {
609 free(data);
610 data = NULL;
611 }
612
613 if (ferror(fp) || feof(fp)) {
614 return false;
615 }
616
617 fflush(fp);
618
619 return true;
620}
Here is the caller graph for this function: