Go to the source code of this file.
Function Documentation
◆ add_connectors()
| bool add_connectors | ( | yubihsm_pkcs11_context * | ctx, |
| int | n_connectors, | ||
| char ** | connector_names, | ||
| yh_connector ** | connectors ) |
Definition at line 2924 of file util_pkcs11.c.

◆ apply_decrypt_mechanism_finalize()
| CK_RV apply_decrypt_mechanism_finalize | ( | yubihsm_pkcs11_op_info * | op_info | ) |
◆ apply_decrypt_mechanism_init()
| CK_RV apply_decrypt_mechanism_init | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 1884 of file util_pkcs11.c.

◆ apply_decrypt_mechanism_update()
| CK_RV apply_decrypt_mechanism_update | ( | yubihsm_pkcs11_op_info * | op_info, |
| CK_BYTE_PTR | in, | ||
| CK_ULONG | in_len ) |
Definition at line 2053 of file util_pkcs11.c.
◆ apply_digest_mechanism_finalize()
| CK_RV apply_digest_mechanism_finalize | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 2163 of file util_pkcs11.c.
◆ apply_digest_mechanism_init()
| CK_RV apply_digest_mechanism_init | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 1902 of file util_pkcs11.c.

◆ apply_digest_mechanism_update()
| CK_RV apply_digest_mechanism_update | ( | yubihsm_pkcs11_op_info * | op_info, |
| CK_BYTE_PTR | in, | ||
| CK_ULONG | in_len ) |
Definition at line 2095 of file util_pkcs11.c.

◆ apply_encrypt_mechanism_update()
| CK_RV apply_encrypt_mechanism_update | ( | yubihsm_pkcs11_op_info * | op_info, |
| CK_BYTE_PTR | in, | ||
| CK_ULONG | in_len ) |
Definition at line 2075 of file util_pkcs11.c.
◆ apply_sign_mechanism_finalize()
| CK_RV apply_sign_mechanism_finalize | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 2117 of file util_pkcs11.c.
◆ apply_sign_mechanism_init()
| CK_RV apply_sign_mechanism_init | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 1763 of file util_pkcs11.c.

◆ apply_sign_mechanism_update()
| CK_RV apply_sign_mechanism_update | ( | yubihsm_pkcs11_op_info * | op_info, |
| CK_BYTE_PTR | in, | ||
| CK_ULONG | in_len ) |
Definition at line 1943 of file util_pkcs11.c.
◆ apply_verify_mechanism_finalize()
| CK_RV apply_verify_mechanism_finalize | ( | yubihsm_pkcs11_op_info * | op_info | ) |
◆ apply_verify_mechanism_init()
| CK_RV apply_verify_mechanism_init | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 1821 of file util_pkcs11.c.

◆ apply_verify_mechanism_update()
| CK_RV apply_verify_mechanism_update | ( | yubihsm_pkcs11_op_info * | op_info, |
| CK_BYTE_PTR | in, | ||
| CK_ULONG | in_len ) |
Definition at line 2007 of file util_pkcs11.c.
◆ check_decrypt_mechanism()
| bool check_decrypt_mechanism | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_PTR | pMechanism ) |
Definition at line 1678 of file util_pkcs11.c.

◆ check_digest_mechanism()
| bool check_digest_mechanism | ( | CK_MECHANISM_PTR | pMechanism | ) |
Definition at line 1725 of file util_pkcs11.c.
◆ check_encrypt_mechanism()
| bool check_encrypt_mechanism | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_PTR | pMechanism ) |
Definition at line 1702 of file util_pkcs11.c.

◆ check_sign_mechanism()
| bool check_sign_mechanism | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_PTR | pMechanism ) |
Definition at line 1646 of file util_pkcs11.c.

◆ check_verify_mechanism()
| bool check_verify_mechanism | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_PTR | pMechanism ) |
Definition at line 1672 of file util_pkcs11.c.
◆ check_wrap_mechanism()
| bool check_wrap_mechanism | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_PTR | pMechanism ) |
Definition at line 1740 of file util_pkcs11.c.

◆ create_session()
| bool create_session | ( | yubihsm_pkcs11_slot * | slot, |
| CK_FLAGS | flags, | ||
| CK_SESSION_HANDLE_PTR | phSession ) |
Definition at line 491 of file util_pkcs11.c.
◆ decrypt_mechanism_cleanup()
| bool decrypt_mechanism_cleanup | ( | yubihsm_pkcs11_op_info * | op_info | ) |
Definition at line 2566 of file util_pkcs11.c.
◆ delete_object_from_cache()
| void delete_object_from_cache | ( | yubihsm_pkcs11_object_desc * | objects, |
| CK_OBJECT_HANDLE | objHandle ) |
Definition at line 1571 of file util_pkcs11.c.
◆ delete_session()
| bool delete_session | ( | yubihsm_pkcs11_context * | ctx, |
| CK_SESSION_HANDLE_PTR | phSession ) |
Definition at line 2831 of file util_pkcs11.c.

◆ destroy_session()
| void destroy_session | ( | yubihsm_pkcs11_context * | ctx, |
| CK_SESSION_HANDLE | hSession ) |
◆ digest_mechanism_cleanup()
| bool digest_mechanism_cleanup | ( | yubihsm_pkcs11_op_info * | op_info | ) |
◆ get_attribute()
| CK_RV get_attribute | ( | CK_ATTRIBUTE_TYPE | type, |
| yh_object_descriptor * | object, | ||
| CK_VOID_PTR | value, | ||
| CK_ULONG_PTR | length, | ||
| yh_session * | session ) |
Definition at line 1455 of file util_pkcs11.c.
◆ get_attribute_ecsession_key()
| CK_RV get_attribute_ecsession_key | ( | CK_ATTRIBUTE_TYPE | type, |
| ecdh_session_key * | key, | ||
| CK_VOID_PTR | value, | ||
| CK_ULONG_PTR | length ) |
Definition at line 1493 of file util_pkcs11.c.

◆ get_digest_bytelength()
| CK_ULONG get_digest_bytelength | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2583 of file util_pkcs11.c.
◆ get_mechanism_info()
| bool get_mechanism_info | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_TYPE | type, | ||
| CK_MECHANISM_INFO_PTR | pInfo ) |
Definition at line 313 of file util_pkcs11.c.
◆ get_mechanism_list()
| CK_RV get_mechanism_list | ( | yubihsm_pkcs11_slot * | slot, |
| CK_MECHANISM_TYPE_PTR | pMechanismList, | ||
| CK_ULONG_PTR | count ) |
Definition at line 73 of file util_pkcs11.c.

◆ get_object_desc()
| yubihsm_pkcs11_object_desc * get_object_desc | ( | yh_session * | session, |
| yubihsm_pkcs11_object_desc * | objects, | ||
| CK_OBJECT_HANDLE | objectHandle ) |
Definition at line 1587 of file util_pkcs11.c.
◆ get_session()
| CK_RV get_session | ( | yubihsm_pkcs11_context * | ctx, |
| CK_SESSION_HANDLE | hSession, | ||
| yubihsm_pkcs11_session ** | session, | ||
| int | session_state ) |
Definition at line 2789 of file util_pkcs11.c.
◆ get_slot()
| yubihsm_pkcs11_slot * get_slot | ( | yubihsm_pkcs11_context * | ctx, |
| CK_ULONG | id ) |
Definition at line 2766 of file util_pkcs11.c.

◆ is_ECDSA_sign_mechanism()
| bool is_ECDSA_sign_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2690 of file util_pkcs11.c.
◆ is_hashed_mechanism()
| bool is_hashed_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2645 of file util_pkcs11.c.
◆ is_HMAC_sign_mechanism()
| bool is_HMAC_sign_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2724 of file util_pkcs11.c.
◆ is_PKCS1v1_5_sign_mechanism()
| bool is_PKCS1v1_5_sign_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2673 of file util_pkcs11.c.
◆ is_PSS_sign_mechanism()
| bool is_PSS_sign_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2707 of file util_pkcs11.c.
◆ is_RSA_decrypt_mechanism()
| bool is_RSA_decrypt_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2627 of file util_pkcs11.c.

◆ is_RSA_sign_mechanism()
| bool is_RSA_sign_mechanism | ( | CK_MECHANISM_TYPE | m | ) |
Definition at line 2605 of file util_pkcs11.c.

◆ parse_ec_generate_template()
| CK_RV parse_ec_generate_template | ( | CK_ATTRIBUTE_PTR | pPublicKeyTemplate, |
| CK_ULONG | ulPublicKeyAttributeCount, | ||
| CK_ATTRIBUTE_PTR | pPrivateKeyTemplate, | ||
| CK_ULONG | ulPrivateKeyAttributeCount, | ||
| yubihsm_pkcs11_object_template * | template ) |
Definition at line 3570 of file util_pkcs11.c.
◆ parse_ec_template()
| CK_RV parse_ec_template | ( | CK_ATTRIBUTE_PTR | pTemplate, |
| CK_ULONG | ulCount, | ||
| yubihsm_pkcs11_object_template * | template ) |
Definition at line 3150 of file util_pkcs11.c.
◆ parse_hex()
| bool parse_hex | ( | CK_UTF8CHAR_PTR | hex, |
| CK_ULONG | hex_len, | ||
| uint8_t * | parsed ) |
Definition at line 464 of file util_pkcs11.c.
◆ parse_hmac_template()
| CK_RV parse_hmac_template | ( | CK_ATTRIBUTE_PTR | pTemplate, |
| CK_ULONG | ulCount, | ||
| yubihsm_pkcs11_object_template * | template, | ||
| bool | generate ) |
Definition at line 3229 of file util_pkcs11.c.

◆ parse_id_value()
| int parse_id_value | ( | void * | value, |
| CK_ULONG | len ) |
Definition at line 3556 of file util_pkcs11.c.
◆ parse_rsa_generate_template()
| CK_RV parse_rsa_generate_template | ( | CK_ATTRIBUTE_PTR | pPublicKeyTemplate, |
| CK_ULONG | ulPublicKeyAttributeCount, | ||
| CK_ATTRIBUTE_PTR | pPrivateKeyTemplate, | ||
| CK_ULONG | ulPrivateKeyAttributeCount, | ||
| yubihsm_pkcs11_object_template * | template ) |
Definition at line 3305 of file util_pkcs11.c.
◆ parse_rsa_template()
| CK_RV parse_rsa_template | ( | CK_ATTRIBUTE_PTR | pTemplate, |
| CK_ULONG | ulCount, | ||
| yubihsm_pkcs11_object_template * | template ) |
Definition at line 2976 of file util_pkcs11.c.
◆ parse_wrap_template()
| CK_RV parse_wrap_template | ( | CK_ATTRIBUTE_PTR | pTemplate, |
| CK_ULONG | ulCount, | ||
| yubihsm_pkcs11_object_template * | template, | ||
| bool | generate ) |
Definition at line 3801 of file util_pkcs11.c.

◆ perform_decrypt()
| CK_RV perform_decrypt | ( | yh_session * | session, |
| yubihsm_pkcs11_op_info * | op_info, | ||
| uint8_t * | ciphertext, | ||
| uint16_t * | ciphertext_len ) |
Definition at line 2463 of file util_pkcs11.c.
◆ perform_digest()
| CK_RV perform_digest | ( | yubihsm_pkcs11_op_info * | op_info, |
| uint8_t * | digest, | ||
| uint16_t * | digest_len ) |
Definition at line 2533 of file util_pkcs11.c.
◆ perform_encrypt()
| CK_RV perform_encrypt | ( | yh_session * | session, |
| yubihsm_pkcs11_op_info * | op_info, | ||
| uint8_t * | plaintext, | ||
| uint16_t * | plaintext_len ) |
Definition at line 2505 of file util_pkcs11.c.
◆ perform_signature()
| CK_RV perform_signature | ( | yh_session * | session, |
| yubihsm_pkcs11_op_info * | op_info, | ||
| uint8_t * | signature, | ||
| uint16_t * | signature_len ) |
Definition at line 2410 of file util_pkcs11.c.
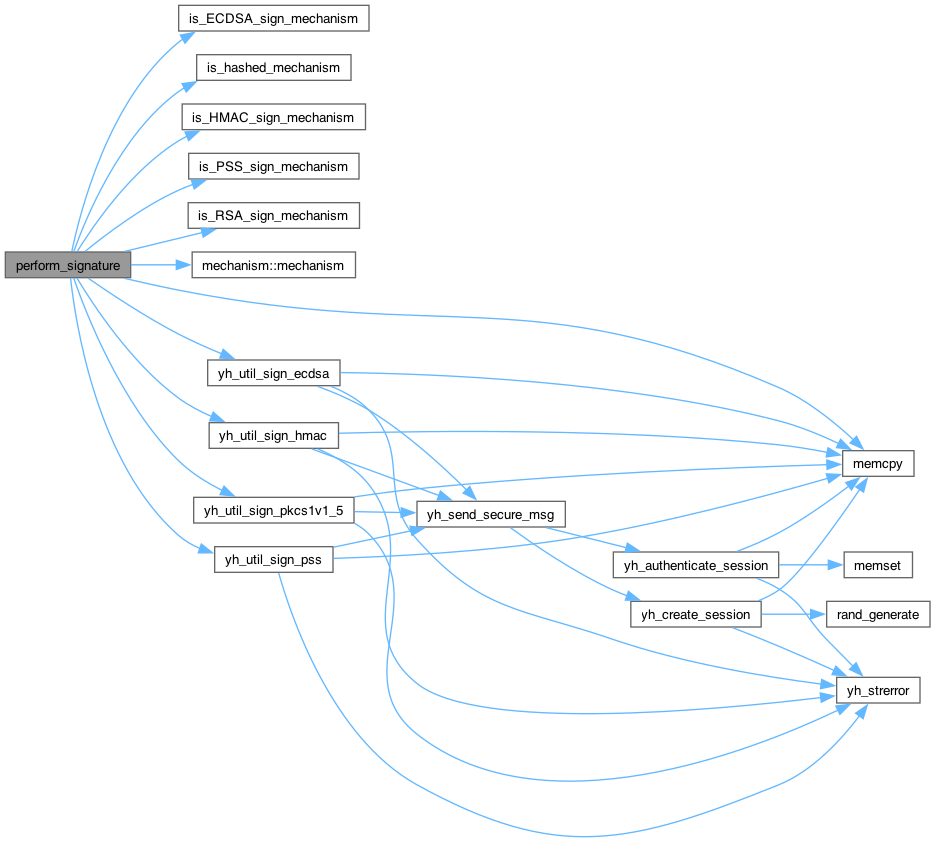
◆ perform_verify()
| CK_RV perform_verify | ( | yh_session * | session, |
| yubihsm_pkcs11_op_info * | op_info, | ||
| uint8_t * | signature, | ||
| uint16_t | signature_len ) |
Definition at line 2225 of file util_pkcs11.c.
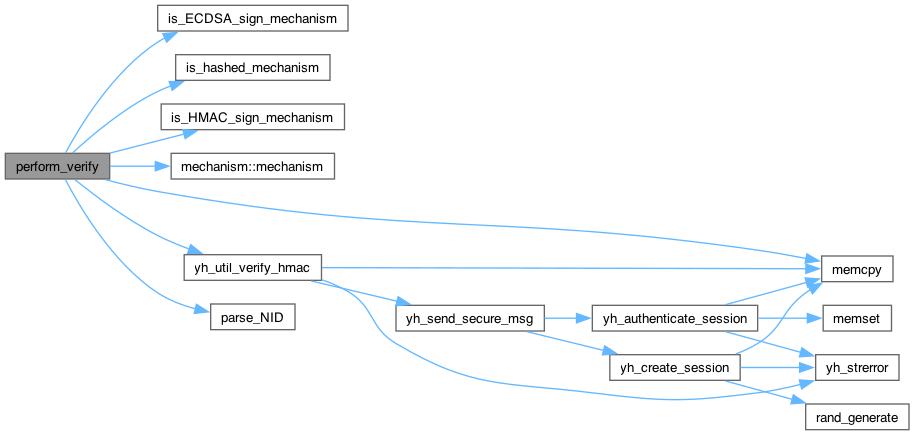
◆ populate_template()
| CK_RV populate_template | ( | int | type, |
| void * | object, | ||
| CK_ATTRIBUTE_PTR | pTemplate, | ||
| CK_ULONG | ulCount, | ||
| yh_session * | session ) |
Definition at line 3872 of file util_pkcs11.c.
◆ release_session()
| void release_session | ( | yubihsm_pkcs11_context * | ctx, |
| yubihsm_pkcs11_session * | session ) |
Definition at line 2850 of file util_pkcs11.c.
◆ release_slot()
| void release_slot | ( | yubihsm_pkcs11_context * | ctx, |
| yubihsm_pkcs11_slot * | slot ) |
Definition at line 2782 of file util_pkcs11.c.
◆ set_native_locking()
| void set_native_locking | ( | yubihsm_pkcs11_context * | ctx | ) |
Definition at line 2916 of file util_pkcs11.c.

◆ set_template_attribute()
| CK_RV set_template_attribute | ( | yubihsm_pkcs11_attribute * | attribute, |
| void * | value ) |
Definition at line 2953 of file util_pkcs11.c.
◆ sign_mechanism_cleanup()
| bool sign_mechanism_cleanup | ( | yubihsm_pkcs11_op_info * | op_info | ) |
◆ validate_derive_key_attribute()
| CK_RV validate_derive_key_attribute | ( | CK_ATTRIBUTE_TYPE | type, |
| void * | value ) |
Definition at line 3940 of file util_pkcs11.c.