Loading...
Searching...
No Matches
#include <assert.h>#include <stdbool.h>#include <stdio.h>#include <stdint.h>#include <stdlib.h>#include <string.h>#include <openssl/ec.h>#include <openssl/evp.h>#include "util.h"#include <yubihsm.h>
Include dependency graph for decrypt_ec.c:
Go to the source code of this file.
Macros | |
| #define | DEFAULT_CONNECTOR_URL "http://127.0.0.1:12345" |
Functions | |
| int | main (void) |
Variables | |
| const char * | key_label = "label" |
| const uint8_t | password [] = "password" |
Macro Definition Documentation
◆ DEFAULT_CONNECTOR_URL
| #define DEFAULT_CONNECTOR_URL "http://127.0.0.1:12345" |
Definition at line 35 of file decrypt_ec.c.
Function Documentation
◆ main()
| int main | ( | void | ) |
Definition at line 41 of file decrypt_ec.c.
41 {
42 yh_connector *connector = NULL;
45
46 uint16_t authkey = 1;
47
48 const char *connector_url;
49
50 connector_url = getenv("DEFAULT_CONNECTOR_URL");
51 if (connector_url == NULL) {
52 connector_url = DEFAULT_CONNECTOR_URL;
53 }
54
57
60
63
67
70
71 uint8_t session_id;
74
76
80
81 uint16_t domain_five = 0;
84
89
91
92 uint8_t public_key[512];
93 size_t public_key_len = sizeof(public_key);
94 yrc =
97
99 for (size_t i = 0; i < public_key_len; i++) {
101 }
103
104 EC_KEY *eckey = EC_KEY_new();
106 EC_POINT *point;
107 EC_GROUP *group = EC_GROUP_new_by_curve_name(nid);
108
109 EC_GROUP_set_asn1_flag(group, nid);
110 EC_KEY_set_group(eckey, group);
111 point = EC_POINT_new(group);
112
113 memmove(public_key + 1, public_key, public_key_len);
114 public_key[0] = 0x04; // hack to make it a valid ec pubkey..
115 public_key_len++;
116
117 EC_POINT_oct2point(group, point, public_key, public_key_len, NULL);
118
119 EC_KEY_set_public_key(eckey, point);
120
121 // Create the context for parameter generation
122 EVP_PKEY_CTX *pctx = EVP_PKEY_CTX_new_id(EVP_PKEY_EC, NULL);
123 assert(pctx != NULL);
124
125 // Initialise the parameter generation
126 assert(EVP_PKEY_paramgen_init(pctx) == 1);
127
128 // We're going to use the ANSI X9.62 Prime 256v1 curve
129 assert(EVP_PKEY_CTX_set_ec_paramgen_curve_nid(pctx, NID_X9_62_prime256v1) ==
130 1);
131
132 // Create the parameter object params
133 EVP_PKEY *params = NULL;
134 assert(EVP_PKEY_paramgen(pctx, ¶ms) == 1);
135
136 // Create the context for the key generation
137 EVP_PKEY_CTX *kctx = EVP_PKEY_CTX_new(params, NULL);
138 assert(kctx != NULL);
139
140 // Generate the key
141 EVP_PKEY *pkey = NULL;
142 assert(EVP_PKEY_keygen_init(kctx) == 1);
143 assert(EVP_PKEY_keygen(kctx, &pkey) == 1);
144
145 // Get the peer's public key, and provide the peer with our public key
146 EVP_PKEY *peerkey = EVP_PKEY_new();
147 assert(peerkey != NULL);
148 assert(EVP_PKEY_set1_EC_KEY(peerkey, eckey) == 1);
149
150 // Create the context for the shared secret derivation
151 EVP_PKEY_CTX *ctx = EVP_PKEY_CTX_new(pkey, NULL);
152 assert(ctx != NULL);
153
154 // Initialise
155 assert(EVP_PKEY_derive_init(ctx) == 1);
156
157 // Provide the peer public key
158 assert(EVP_PKEY_derive_set_peer(ctx, peerkey) == 1);
159
160 uint8_t secret[64];
161 size_t secret_len = sizeof(secret_len);
162
163 // Determine buffer length for shared secret
164 assert(EVP_PKEY_derive(ctx, NULL, &secret_len));
165
166 // Derive the shared secret
167 assert(EVP_PKEY_derive(ctx, secret, &secret_len) == 1);
168
169 EC_KEY *eckey2 = EVP_PKEY_get1_EC_KEY(pkey);
171
174
175 pubkey_len = EC_POINT_point2oct(group, pub, POINT_CONVERSION_UNCOMPRESSED,
176 pubkey, pubkey_len, NULL);
177 assert(pubkey_len == 65);
178
179 uint8_t computed_secret[128];
180 size_t computed_secret_len = sizeof(computed_secret);
182 computed_secret, &computed_secret_len);
184
185 assert(computed_secret_len == secret_len);
186 assert(memcmp(secret, computed_secret, computed_secret_len) == 0);
187
189
190 EVP_PKEY_CTX_free(ctx);
191 EVP_PKEY_free(peerkey);
192 EVP_PKEY_free(pkey);
193 EVP_PKEY_CTX_free(kctx);
194 EVP_PKEY_free(params);
195 EVP_PKEY_CTX_free(pctx);
196 EC_POINT_free(point);
197 EC_KEY_free(eckey);
198 EC_KEY_free(eckey2);
199 EC_GROUP_free(group);
200
203
206
207 yh_disconnect(connector);
209
212
213 return 0;
214}
LOGGING_API void printf(Category category, const char *format,...)
Definition Logging.cpp:30
Definition Benchmark.cpp:5
Definition internal.h:37
Definition internal.h:25
account_query_db::get_accounts_by_authorizers_params params
Definition test_account_query_db.cpp:20
yh_rc yh_util_derive_ecdh(yh_session *session, uint16_t key_id, const uint8_t *in, size_t in_len, uint8_t *out, size_t *out_len)
Definition yubihsm.c:2174
yh_rc yh_util_generate_ec_key(yh_session *session, uint16_t *key_id, const char *label, uint16_t domains, const yh_capabilities *capabilities, yh_algorithm algorithm)
Definition yubihsm.c:1913
yh_rc yh_create_session_derived(yh_connector *connector, uint16_t authkey_id, const uint8_t *password, size_t password_len, bool recreate, yh_session **session)
Definition yubihsm.c:593
yh_rc yh_string_to_domains(const char *domains, uint16_t *result)
Definition yubihsm.c:4535
yh_rc yh_init_connector(const char *url, yh_connector **connector)
Definition yubihsm.c:4024
yh_rc yh_util_get_public_key(yh_session *session, uint16_t id, uint8_t *data, size_t *data_len, yh_algorithm *algorithm)
Definition yubihsm.c:1216
yh_rc yh_string_to_capabilities(const char *capability, yh_capabilities *result)
Definition yubihsm.c:4115
yh_rc yh_get_session_id(yh_session *session, uint8_t *sid)
Definition yubihsm.c:2915
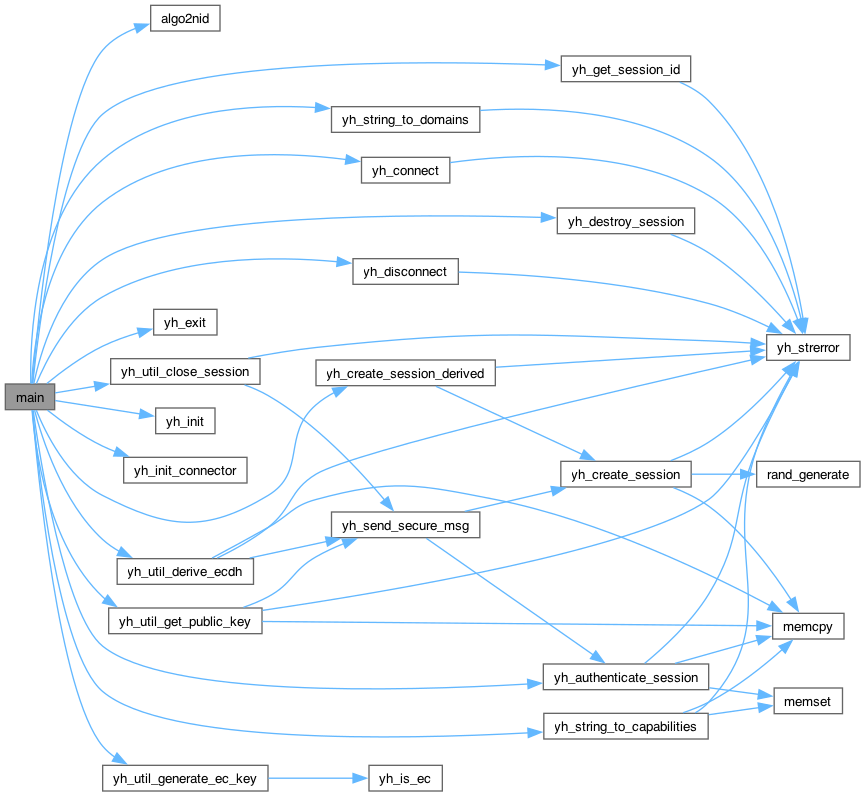
Here is the call graph for this function:
Variable Documentation
◆ key_label
| const char* key_label = "label" |
Definition at line 38 of file decrypt_ec.c.
◆ password
| const uint8_t password[] = "password" |
Definition at line 39 of file decrypt_ec.c.