contains only the public point of an elliptic curve key. More...
#include <elliptic_r1.hpp>
Public Member Functions | |
| public_key () | |
| public_key (const public_key &k) | |
| ~public_key () | |
| bool | verify (const fc::sha256 &digest, const signature &sig) |
| public_key_data | serialize () const |
| operator public_key_data () const | |
| public_key (const public_key_data &v) | |
| public_key (const public_key_point_data &v) | |
| public_key (const compact_signature &c, const fc::sha256 &digest, bool check_canonical=true) | |
| bool | valid () const |
| public_key | mult (const fc::sha256 &offset) |
| public_key | add (const fc::sha256 &offset) const |
| public_key (public_key &&pk) | |
| public_key & | operator= (public_key &&pk) |
| public_key & | operator= (const public_key &pk) |
| std::string | to_base58 () const |
| Allows to convert current public key object into base58 number. | |
Static Public Member Functions | |
| static public_key | from_base58 (const std::string &b58) |
Friends | |
| class | private_key |
| bool | operator== (const public_key &a, const public_key &b) |
| bool | operator!= (const public_key &a, const public_key &b) |
| compact_signature | signature_from_ecdsa (const EC_KEY *key, const public_key_data &pub_data, fc::ecdsa_sig &sig, const fc::sha256 &d) |
Detailed Description
Definition at line 32 of file elliptic_r1.hpp.
Constructor & Destructor Documentation
◆ public_key() [1/6]
| fc::crypto::r1::public_key::public_key | ( | ) |
Definition at line 455 of file elliptic_r1.cpp.
◆ public_key() [2/6]
| fc::crypto::r1::public_key::public_key | ( | const public_key & | k | ) |
Definition at line 573 of file elliptic_r1.cpp.
◆ ~public_key()
| fc::crypto::r1::public_key::~public_key | ( | ) |
Definition at line 458 of file elliptic_r1.cpp.
◆ public_key() [3/6]
| fc::crypto::r1::public_key::public_key | ( | const public_key_data & | v | ) |
Definition at line 474 of file elliptic_r1.cpp.
◆ public_key() [4/6]
| fc::crypto::r1::public_key::public_key | ( | const public_key_point_data & | v | ) |
Definition at line 461 of file elliptic_r1.cpp.
◆ public_key() [5/6]
| fc::crypto::r1::public_key::public_key | ( | const compact_signature & | c, |
| const fc::sha256 & | digest, | ||
| bool | check_canonical = true ) |
Definition at line 516 of file elliptic_r1.cpp.
◆ public_key() [6/6]
| fc::crypto::r1::public_key::public_key | ( | public_key && | pk | ) |
Definition at line 577 of file elliptic_r1.cpp.
Member Function Documentation
◆ add()
| public_key fc::crypto::r1::public_key::add | ( | const fc::sha256 & | offset | ) | const |
Definition at line 193 of file elliptic_em_impl_pub.cpp.
◆ from_base58()
|
static |
Definition at line 318 of file elliptic_r1.cpp.
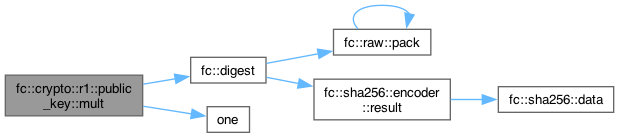
◆ mult()
| public_key fc::crypto::r1::public_key::mult | ( | const fc::sha256 & | offset | ) |
Definition at line 235 of file elliptic_r1.cpp.
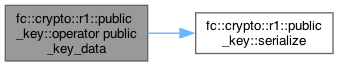
◆ operator public_key_data()
|
inline |
Definition at line 41 of file elliptic_r1.hpp.
◆ operator=() [1/2]
| public_key & fc::crypto::r1::public_key::operator= | ( | const public_key & | pk | ) |
Definition at line 600 of file elliptic_r1.cpp.
◆ operator=() [2/2]
| public_key & fc::crypto::r1::public_key::operator= | ( | public_key && | pk | ) |
Definition at line 590 of file elliptic_r1.cpp.
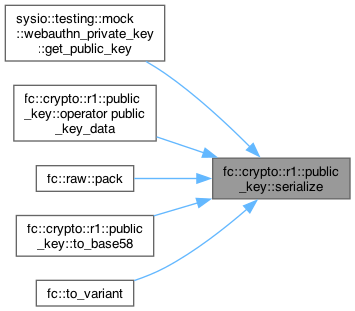
◆ serialize()
| public_key_data fc::crypto::r1::public_key::serialize | ( | ) | const |
Definition at line 438 of file elliptic_r1.cpp.
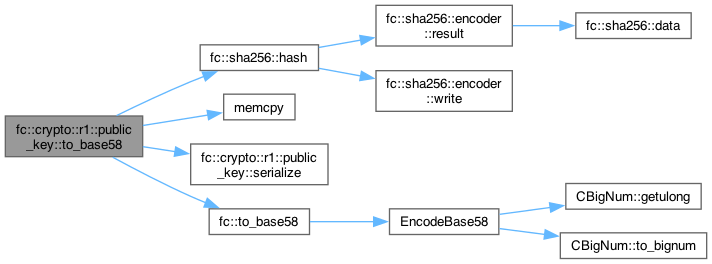
◆ to_base58()
| std::string fc::crypto::r1::public_key::to_base58 | ( | ) | const |
Definition at line 307 of file elliptic_r1.cpp.
◆ valid()
| bool fc::crypto::r1::public_key::valid | ( | ) | const |
Definition at line 258 of file elliptic_r1.cpp.
◆ verify()
| bool fc::crypto::r1::public_key::verify | ( | const fc::sha256 & | digest, |
| const signature & | sig ) |
Definition at line 433 of file elliptic_r1.cpp.
Friends And Related Symbol Documentation
◆ operator!=
|
friend |
Definition at line 60 of file elliptic_r1.hpp.
◆ operator==
|
friend |
Definition at line 56 of file elliptic_r1.hpp.
◆ private_key
|
friend |
Definition at line 70 of file elliptic_r1.hpp.
◆ signature_from_ecdsa
|
friend |
Definition at line 136 of file elliptic_r1.cpp.
The documentation for this class was generated from the following files:
- libraries/fc/include/fc/crypto/elliptic_r1.hpp
- libraries/fc/src/crypto/elliptic_em_impl_pub.cpp
- libraries/fc/src/crypto/elliptic_impl_pub.cpp
- libraries/fc/src/crypto/elliptic_r1.cpp